- All templates
- Activity diagram templates
- Activity diagram login
About this activity diagram for login
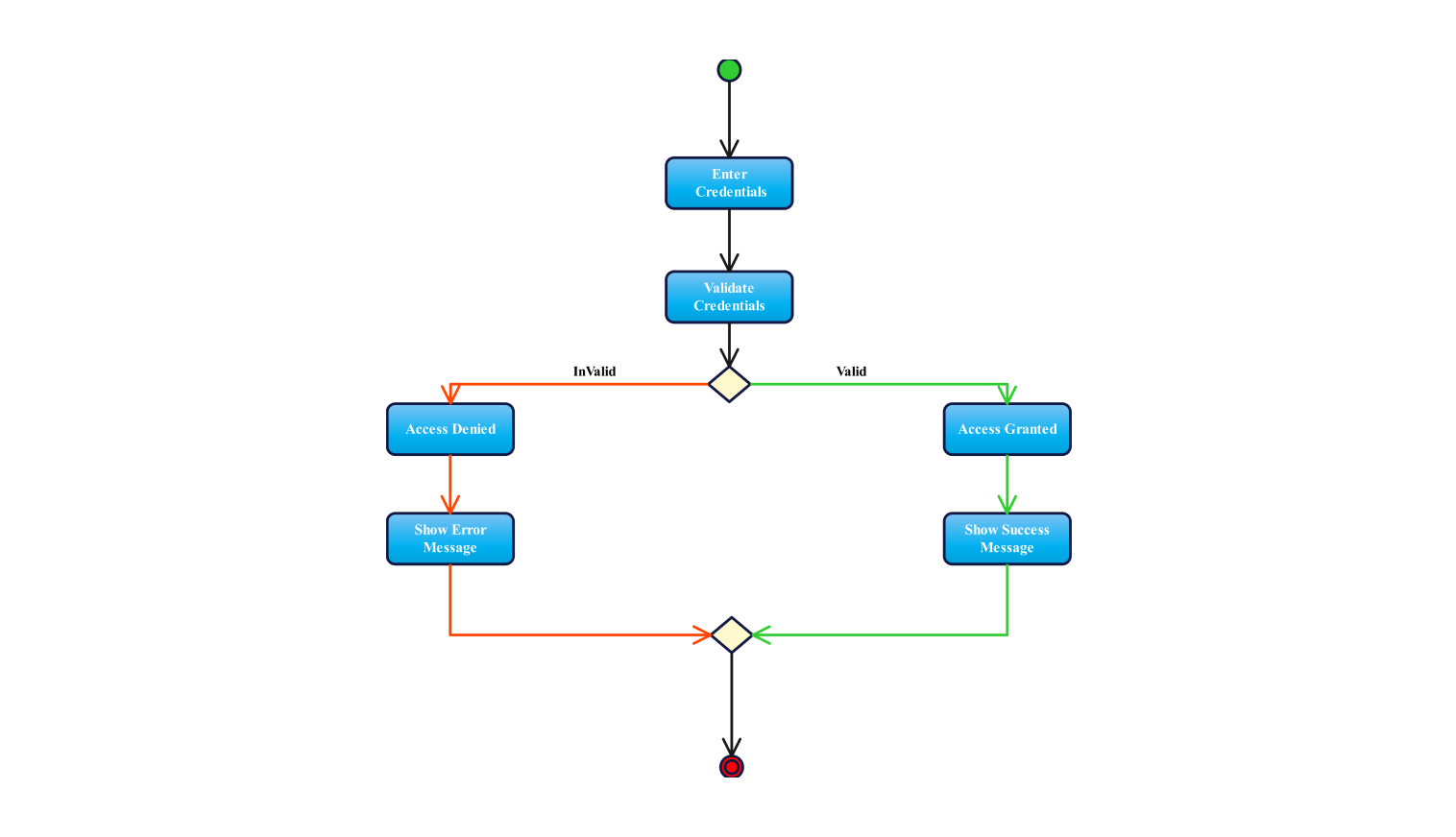
This activity diagram shows the login process in a system. It visually illustrates the steps from entering credentials to the final access decision. The diagram starts with the "enter credentials" action, which is when users enter their login data.
The next stage is "validate credentials." It's a key decision point. It checks if the entered credentials are authentic. There are two possible results for this decision node: either the credentials are valid or they are not.
In case your credentials are considered invalid, the way leads to "access denied". At this stage, the user is informed that their login has failed. Then an "error message" pops up telling them what went wrong.
Afterward in the process, the system prompts the user to try out a different password. However, if the credentials are valid, the process will reach "access granted". This action proves that the user is already logged into a system.
Then, in a subsequent step, the system will display a message that says "success message" depicting that access is granted. This serves as positive feedback and informs the user that they have successfully been authenticated.
Both ways, whether access is allowed or not, converge at the same endpoint thus making sure that the process is completed neatly no matter what the result may be.
Successful and error messages play a key role in user experience because they offer instant feedback on attempted logins. This figure ensures a clear, simple logging process for users. It allows them to easily spot and avoid any problems when authenticating.
How to use this template
Click on Use this template to use it. After the template opens, customize the diagram. Drag and drop new shapes from the libraries on the left to fit your system's needs.
Edit the text. Style the boxes, lines, and text by clicking on the elements. You can save some common elements in your library. You can reuse them when creating similar diagrams.
Click the theme icon if you want to use the “one-click beautify” feature. This feature instantly changes the colors, fonts, and layout of your picture. It makes it look professional.
You can export your file in several formats for later use. Click Export to select the format (.eddx, .pdf, .png, .jpg).
Benefits of the activity diagram
The activity diagram designed for logging in has several benefits. To begin with, it gives a clear visual representation of the login process, making it easy to understand user authentication stages. This clarity enables developers and stakeholders to identify any existing problems in the process or suggest improvements.
Moreover, the diagram improves communication between team members. This is achieved by providing a shared visual language to everyone engaged in the project concerning how to log in. This decreases misinterpretation and allows for better cooperation.
More so, the diagram identifies security loopholes. While laying out the whole procedure of logging in, programmers may locate areas where there are no adequate safeguards to ensure that an authentication system is more secure.
It also helps capture the system requirements and methods for future maintenance. The document is essential for the professionals in training since they are required by law when starting.
FAQs about the activity diagram
-
What activity diagram for a login process?
The login process can be represented by an activity diagram that shows a series of actions performed during user attempts to log into the system. It illustrates how one starts by entering their credentials, then these are validated before access is either granted or denied depending on the outcome of its validity check.
-
How to draw an activity diagram?
To come up with an activity diagram, you need to take five steps: 1. identify the activities and actions, 2. define the control flow, 3. incorporate the decision points, 4. include the starting and ending points, and 5. arrange the swim lanes.
-
Can activity diagrams for login processes be used in different types of systems?
Without a doubt, activity diagrams can be adaptable and may be deployed on login processes within different systems such as desktop applications, mobile apps, and websites. The login process can always be documented in a standardized manner irrespective of the platform used for authentication.
Related templates
Get started with EdrawMax today
Create 210 types of diagrams online for free.
Draw a diagram free Draw a diagram free Draw a diagram free Draw a diagram free Draw a diagram free