- All templates
- Network diagram templates
- Network diagram security
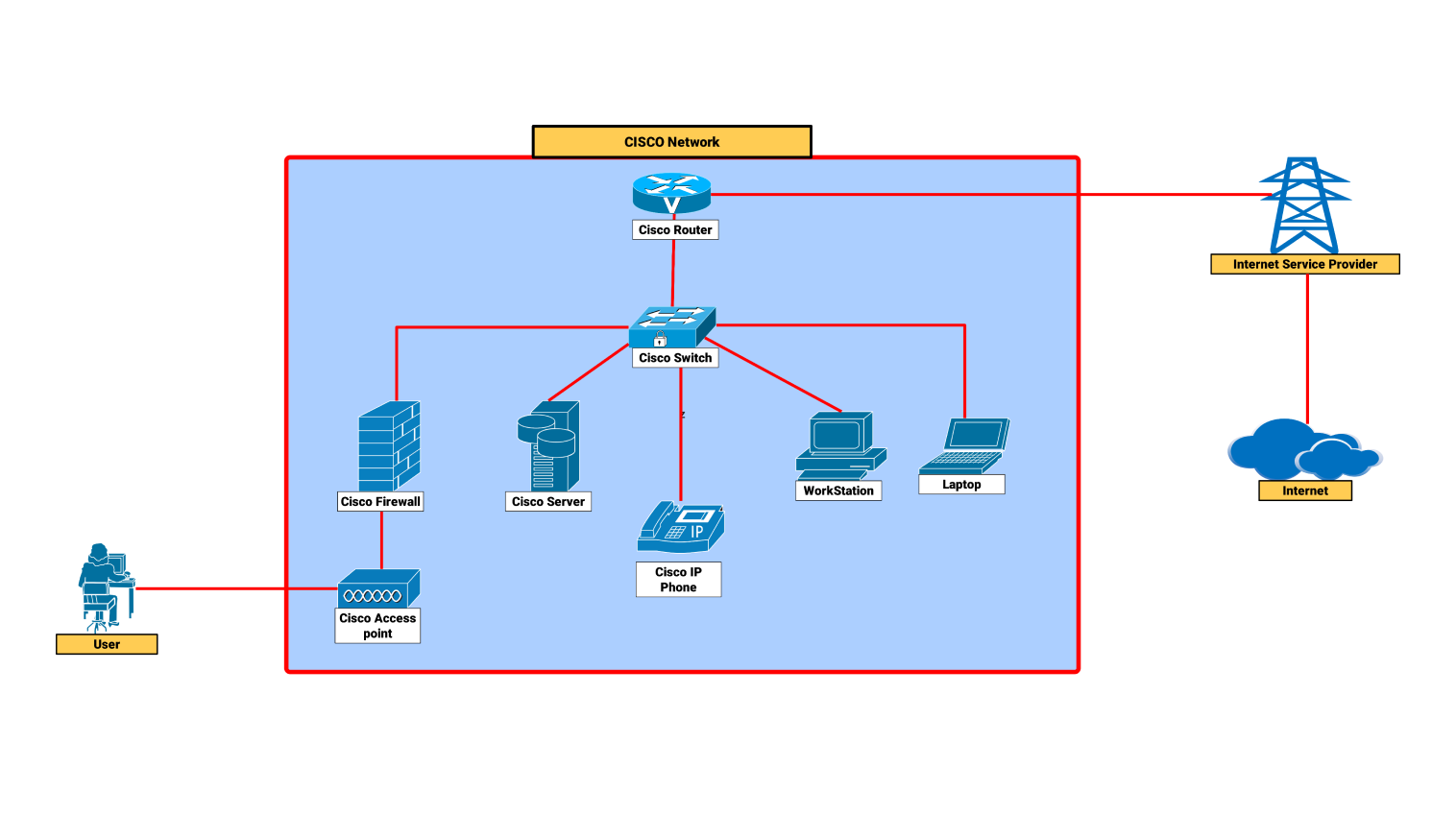
About this network security diagram
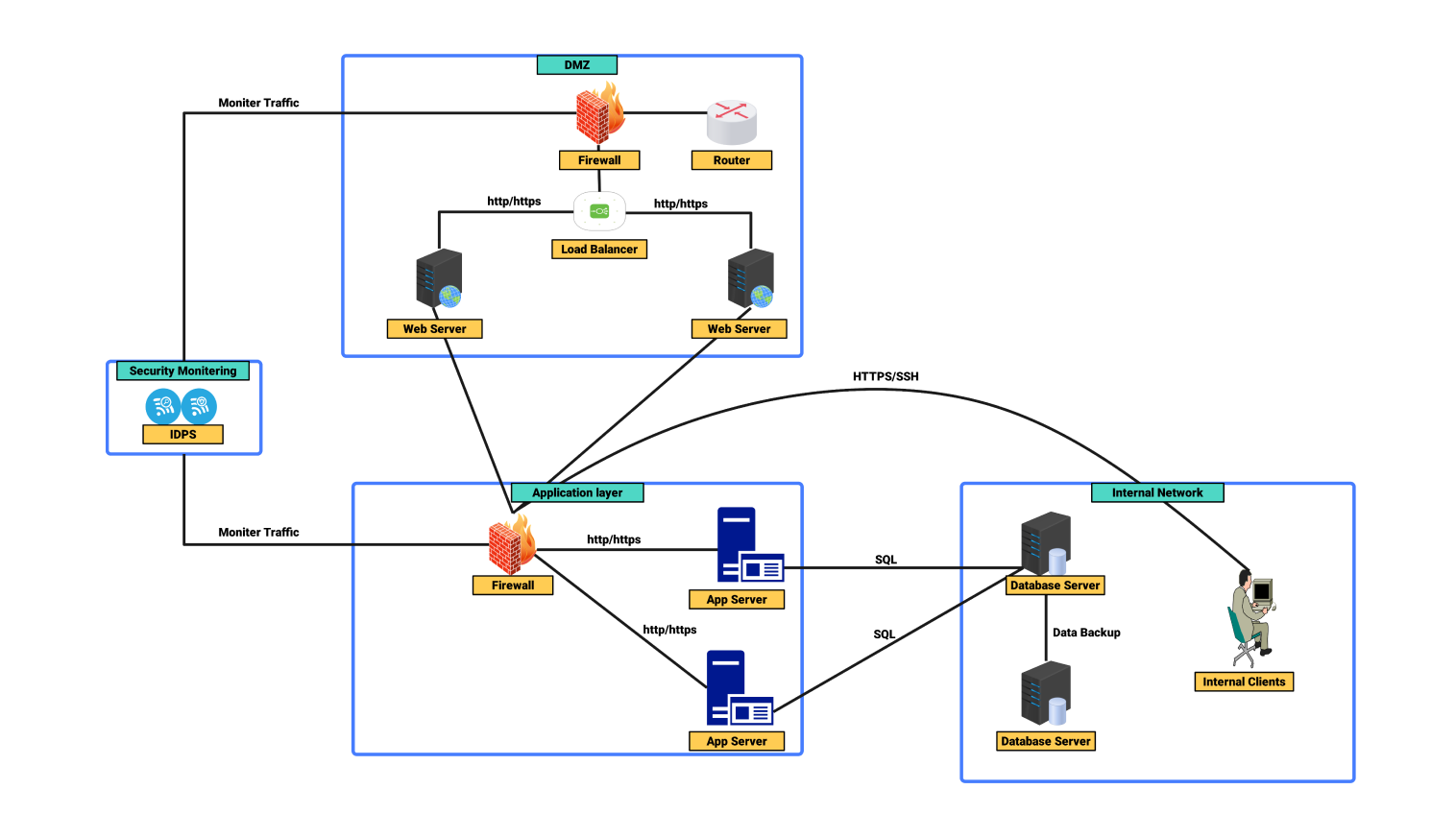
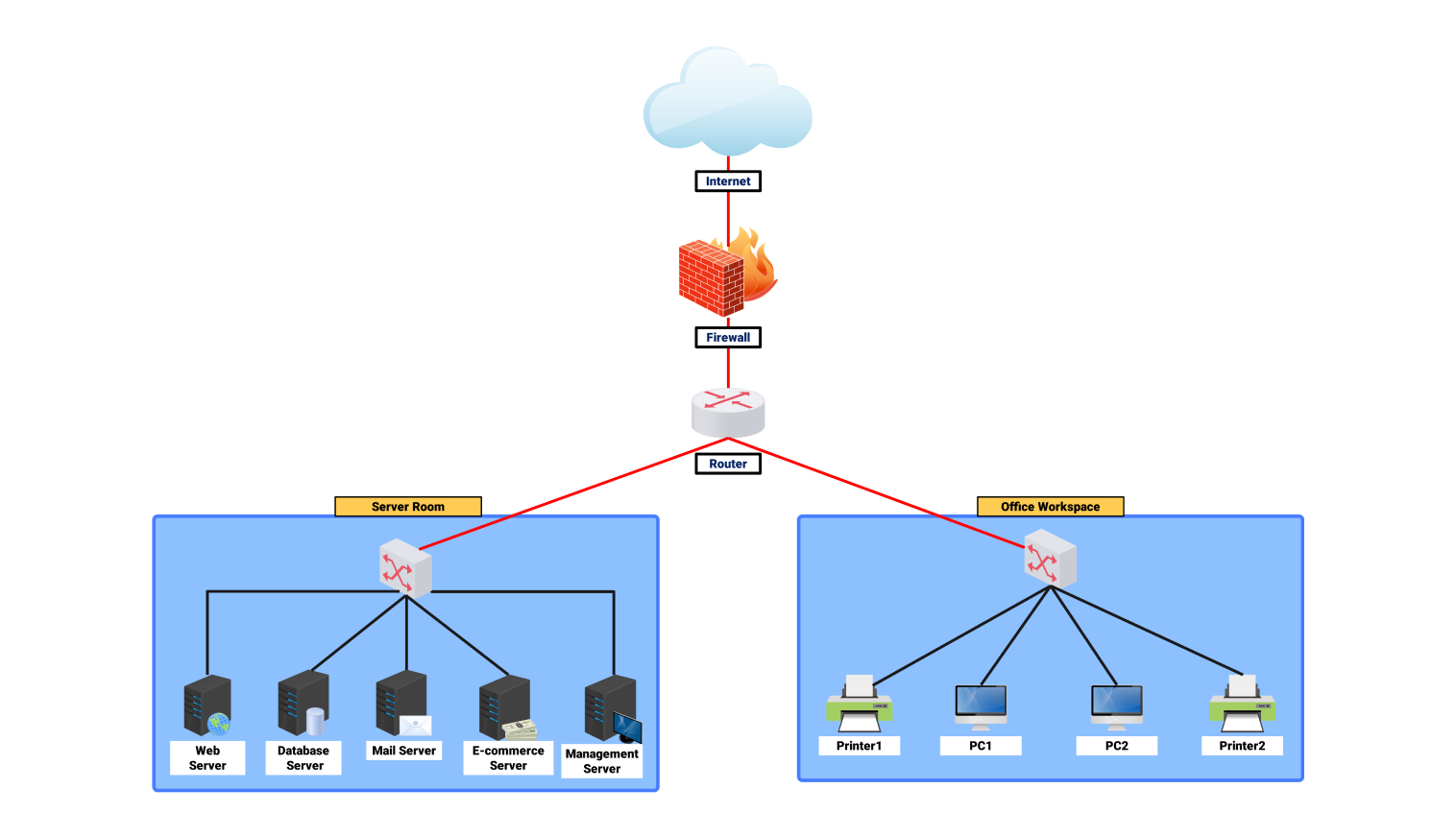
This network security diagram explains the architecture used for security and managing online applications, databases, and internal users in the workplace. It underlines the value of multiple security levels offering defense-in-depth and components to guarantee the confidential flow of data and prevent unauthorized access.
A demilitarized zone (DMZ) containing the web servers is at the top. These servers handle HTTP/HTTPS requests from outside clients. The DMZ is protected by a firewall that filters incoming and outgoing traffic.
The filtering allows only genuine requests to reach the servers. A router in the DMZ routes traffic to the suitable web server based on the request.
A load balancer in the DMZ efficiently distributes incoming traffic across several web servers. Its main purpose is to make sure that not all the traffic is sent to a single server as this might cause overloading. This results in optimal performance and availability.
This configuration improves the system's scalability and redundancy. These factors become critical when dealing with changing traffic loads is concerned.
The application layer is present below the DMZ. It contains another firewall responsible for its protection. This farewell is present behind the web servers. This layer includes application servers, which execute business logic and handle HTTP/HTTPS traffic from web servers.
The application servers communicate with the database servers through secure SQL connections to retrieve or update data upon user requests.
The internal network is dedicated to the database servers and internal users. Database servers store and handle important data. They communicate with the application servers and execute SQL queries. Data is backed up regularly to ensure the system’s integrity and availability in case of failure.
The intrusion detection and prevention system (IDPS) is present to provide effective security measures. It enhances security by monitoring network traffic for illegal activity. The IDPS is connected to the security monitoring system to give real-time alerts and responses to potential threats. It helps in securing the network from intrusions and attacks.
This network diagram follows a multi-layered security architecture that employs firewalls, load balancers, and a security monitoring system. These work together to secure web applications, databases, and internal clients. The diagram shows the efficient network division to reduce vulnerabilities and maintain data integrity and anonymity
Related templates
Get started with EdrawMax today
Create 210 types of diagrams online for free.
Draw a diagram free Draw a diagram free Draw a diagram free Draw a diagram free Draw a diagram free