An effective cyber risk mitigation is indispensable for businesses of all sizes. Safeguarding sensitive data and operations from evolving cyber threats is a top priority. This comprehensive guide explores essential strategies and best practices to fortify your organization's defenses. From proactive threat assessments to robust security protocols, learn how to navigate the digital realm with confidence. Stay ahead of potential risks and ensure long-term business resilience in an ever-changing technological landscape.
Cyber risk refers to the potential harm or financial loss an individual, organization, or society may incur due to a breach or failure in their digital security measures. It encompasses a wide range of threats, including hacking, data breaches, malware attacks, and other cyber incidents. As technology advances, understanding and managing cyber risk has become crucial for safeguarding sensitive information and maintaining the integrity of digital operations.
In this article
Part 1. Types of Cyber Risk

Different forms of third-party cyber risks emerge, each posing unique challenges to digital security. These categories of threats encompass:
- Malware - Harmful software that infiltrates systems and exploits weaknesses.
- Phishing - Tricking users to acquire sensitive information via emails or deceptive websites.
- Ransomware - Encrypting data and demanding a payment for decryption.
- Data Breaches - Unauthorized access and exposure of confidential information.
- Denial-of-Service Attacks - Overloading systems to disrupt their availability.
- Insider Threats - Misuse of access by employees and authorized users.
It is imperative to comprehend these risks in order to formulate effective cybersecurity strategies.
Part 2. Role of Cyber Risk Mitigation
Understanding cyber risk mitigation is imperative in today's digitally-driven landscape. It involves identifying, assessing, and implementing strategies to minimize the potential impact of cyber threats on an organization. This proactive approach empowers businesses to safeguard sensitive data, systems, and operations.
By staying ahead of potential risks, companies can ensure operational continuity and maintain trust with stakeholders in an ever-evolving technological environment.
Part 3. How Can Cyber Risk Mitigation Help Businesses
In an era dominated by digital connectivity, cyber risk mitigation plays a pivotal role in safeguarding businesses. Here's how it can help:
- Protects Sensitive Data: Shields valuable information from unauthorized access or theft.
- Preserves Reputation: Prevents breaches that could tarnish a company's image and erode trust.
- Ensures Regulatory Compliance: Helps adhere to data protection laws and industry regulations.
- Safeguards Financial Stability: Minimizes the financial impact of cyber incidents, preserving profitability.
- Maintains Operational Continuity: Prevents disruptions, ensuring seamless business operations.
By employing robust mitigation strategies, businesses fortify their resilience against evolving cyber threats.
Part 4. Creating a Risk Management Chart using EdrawMax
In an age where cyber threats loom large, creating a robust cybersecurity framework is paramount for safeguarding sensitive information and ensuring business continuity. EdrawMax emerges as a powerful tool in this endeavor, offering a user-friendly platform to design and implement effective security strategies.
With its intuitive interface and diverse range of templates, EdrawMax empowers organizations to tailor their cybersecurity framework to their specific needs and industry requirements. This ensures a comprehensive defense against evolving cyber risks, from malware attacks to data breaches, providing businesses with the peace of mind that their digital assets are well-protected.
Here are the steps to create a basic cyber security framework diagram using EdrawMax:
Step 1: Launch the EdrawMax application on your computer. Click on "New" if you want to start working on a blank canvas. Or switch to the “Template” gallery and search for "Network Security" or "Cybersecurity" from the available template categories. Select a template that suits your needs.
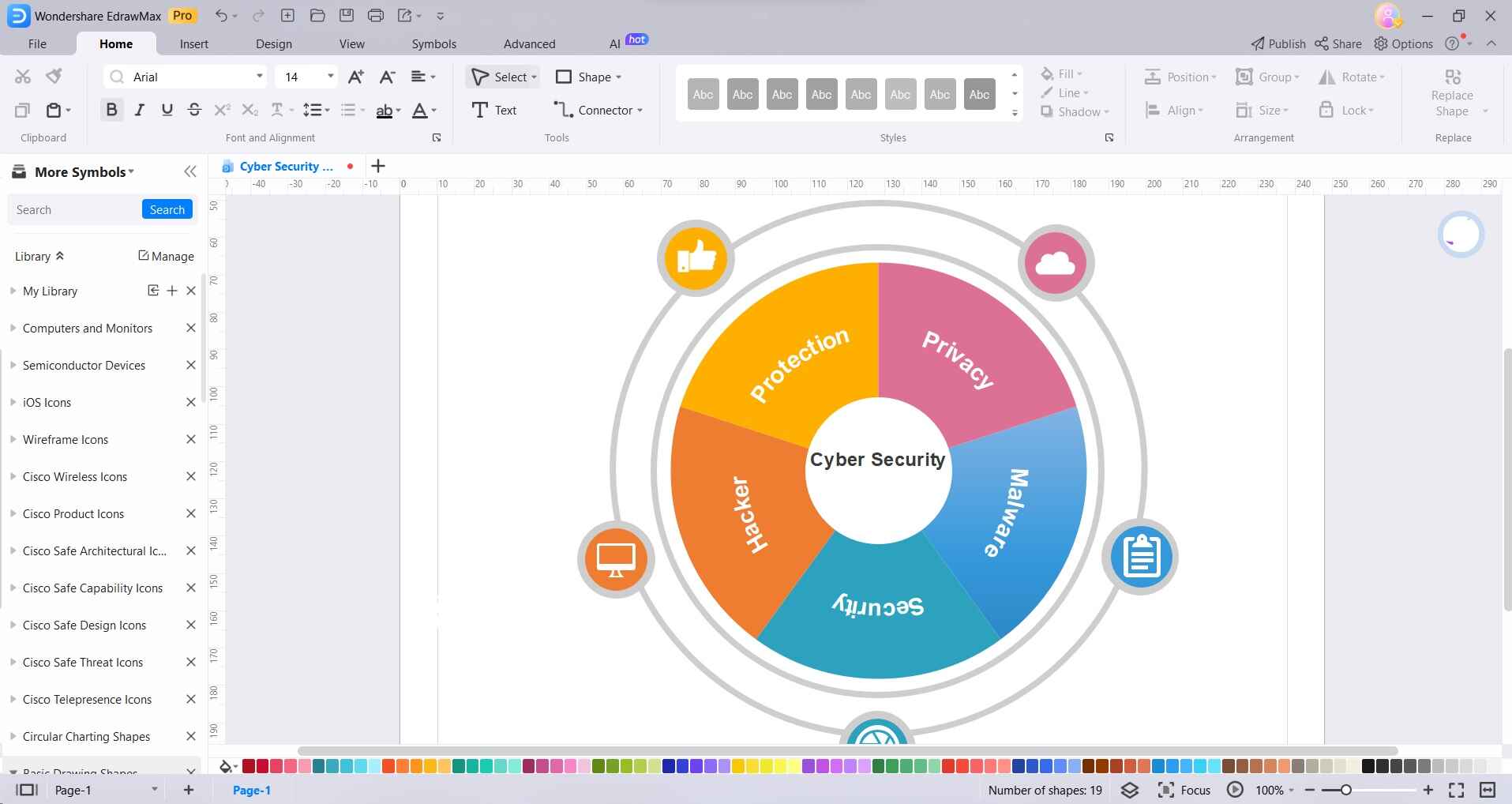
Step 2: Drag and drop the desired shapes and elements from the template onto the canvas. These may include icons representing firewalls, antivirus software, network devices, etc. Double-click on the shapes to edit text, and labels, or add specific details to each element. You can also change colors, resize, or rotate shapes as needed.
Step 3: Use lines or connectors to illustrate the relationships between different components. Click on the connector tool, then click and drag from one element to another.
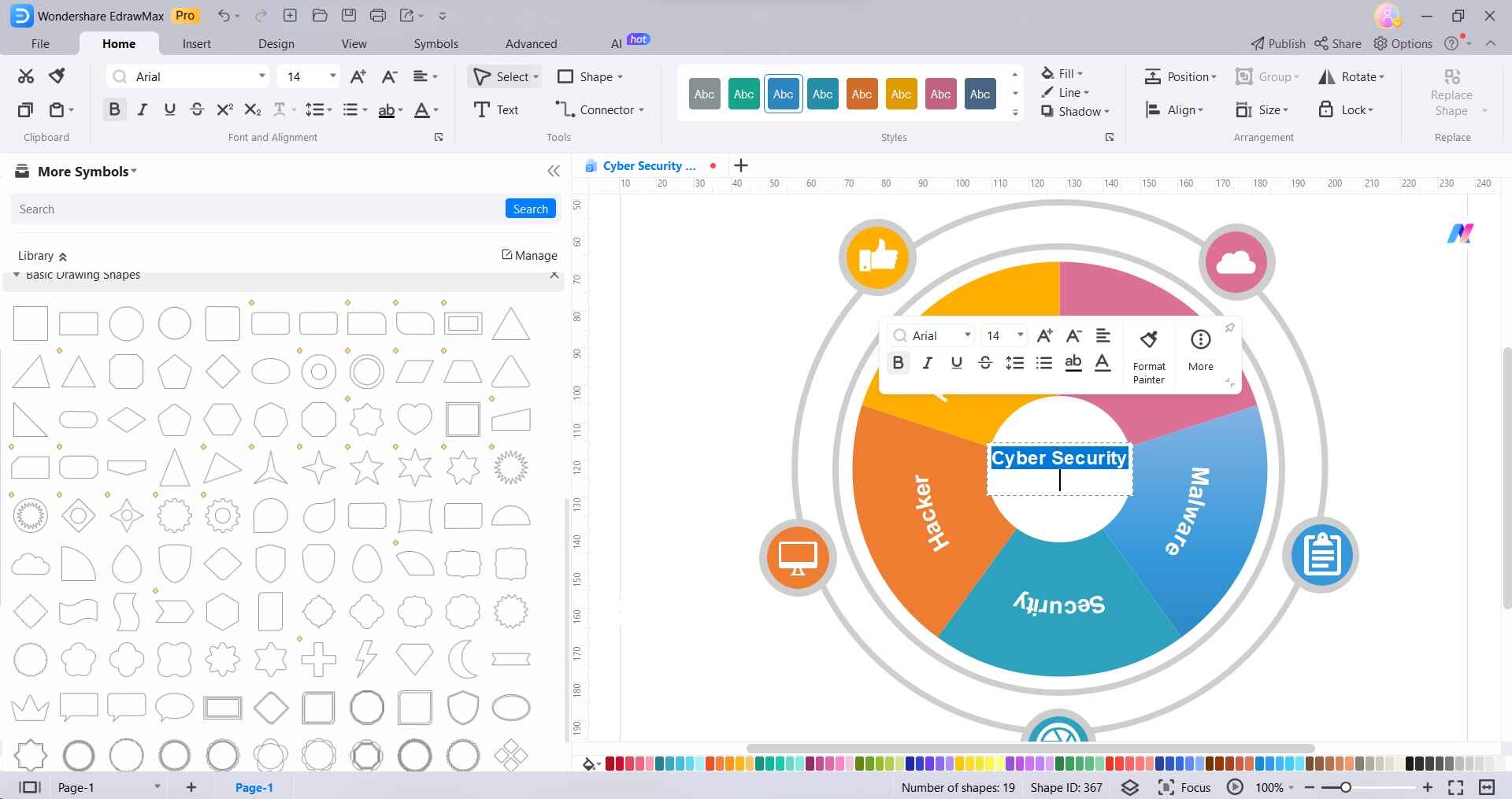
Step 4: To enhance visual clarity or align with your organization's branding, you can customize the color scheme of the elements in your diagram. Click on a shape or element, then navigate to the "Styles" option in the toolbar. Choose from the available color options or use the color picker to select a custom hue. Apply the desired color to the shape, and repeat this process for other elements as needed.
Step 5: Once your diagram is complete, click on "File" and then "Save" to save the diagram in a format of your choice (e.g., .eddx, .png, .jpg). You can also export it for sharing or further editing.
With these steps, you'll have created a basic cybersecurity framework diagram using EdrawMax. Remember, EdrawMax offers a range of features and customization options, so feel free to explore and make your diagram as detailed and tailored as needed.
Conclusion
With cyberattacks on the rise, protecting your business from online threats is more important than ever. EdrawMax makes building a robust cybersecurity strategy easy. Its intuitive interface and variety of templates simplify the process of creating a plan to keep your data safe. This software enables companies to strengthen their digital defenses and remain current on cybersecurity best practices. By leveraging EdrawMax, organizations can tackle cyber risks with confidence, safeguarding critical information in our increasingly interconnected digital landscape.