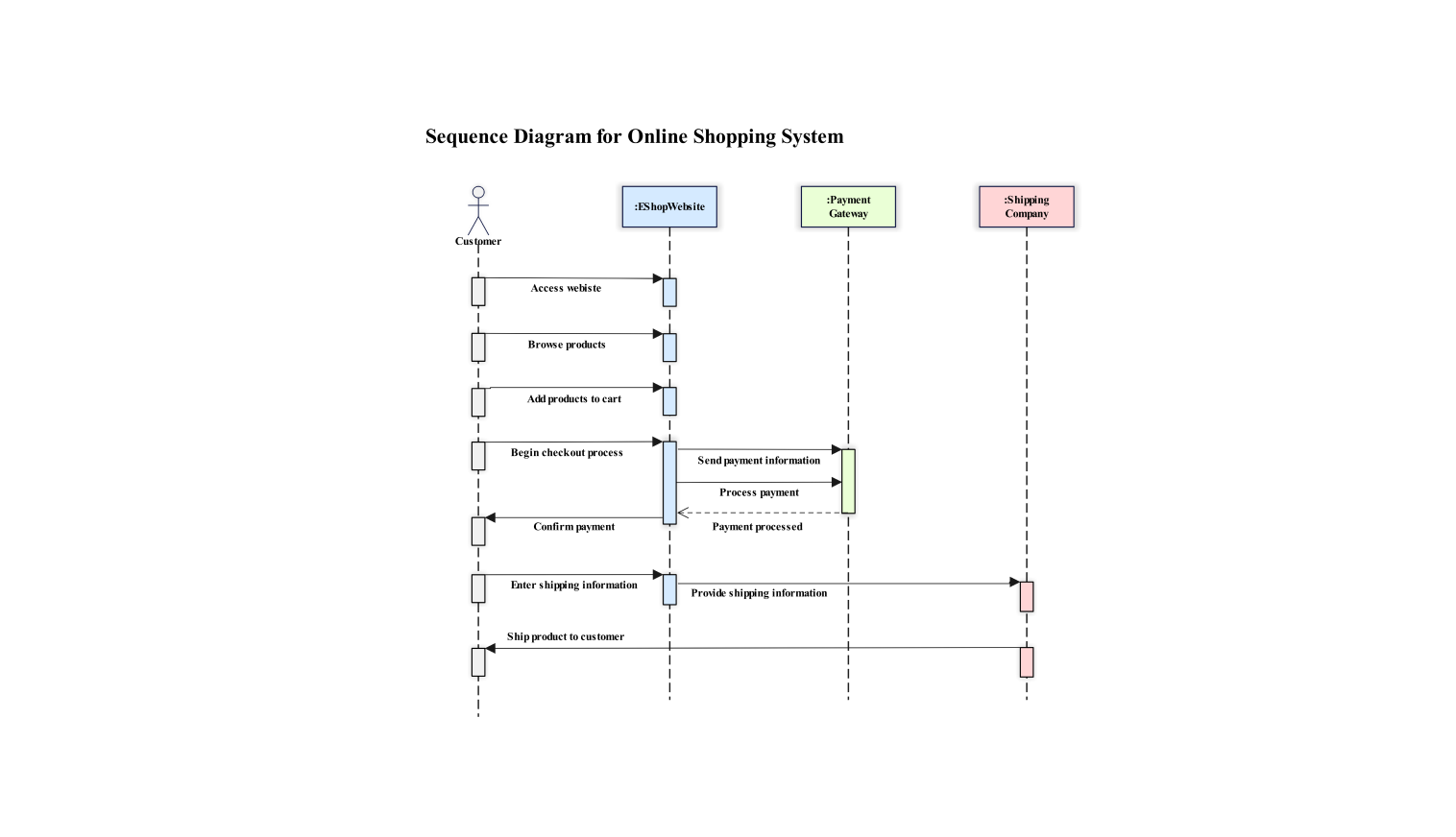
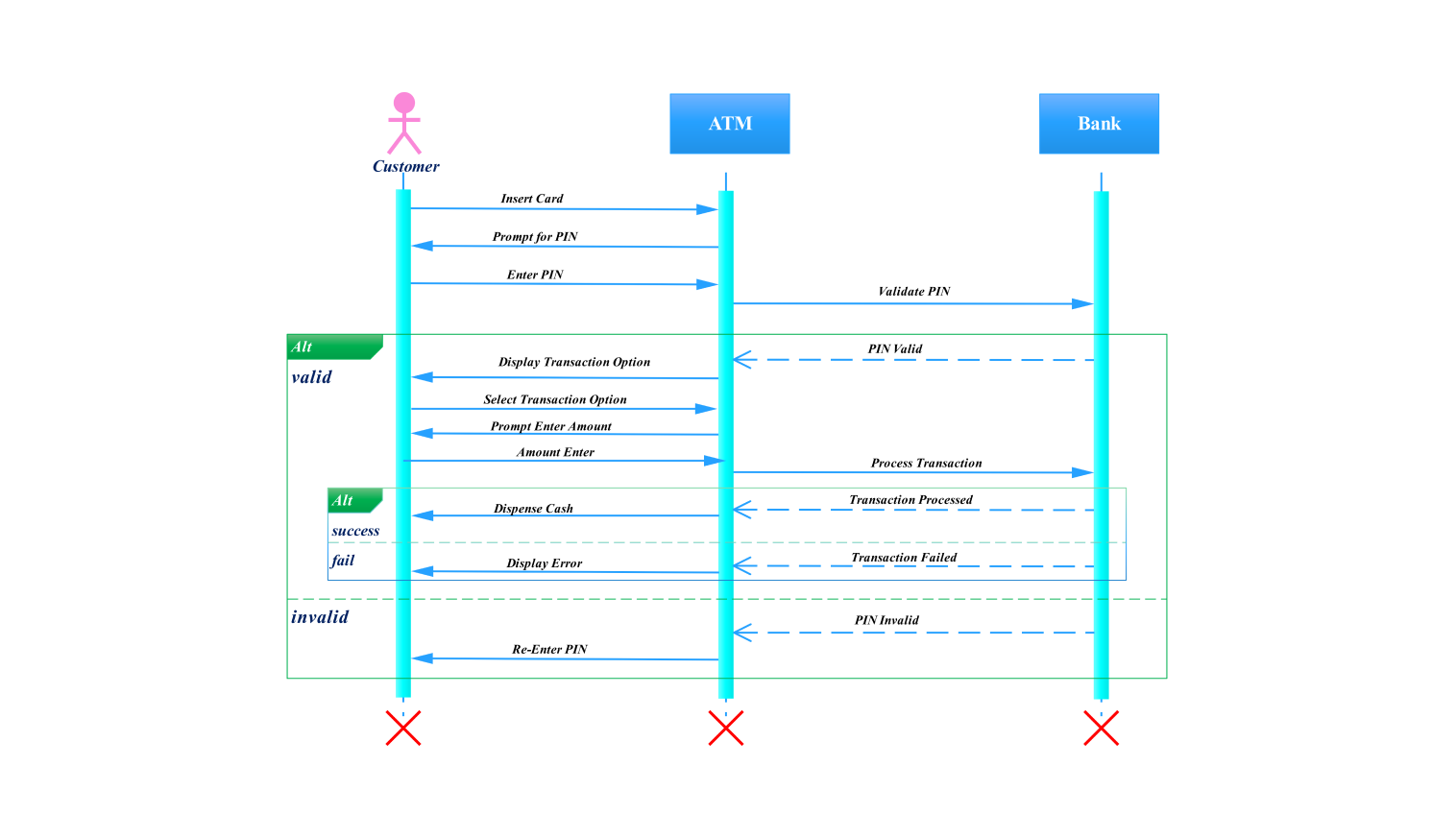
- All templates
- Sequence diagram templates
- Sequence diagram authentication
About this sequence diagram for authentication
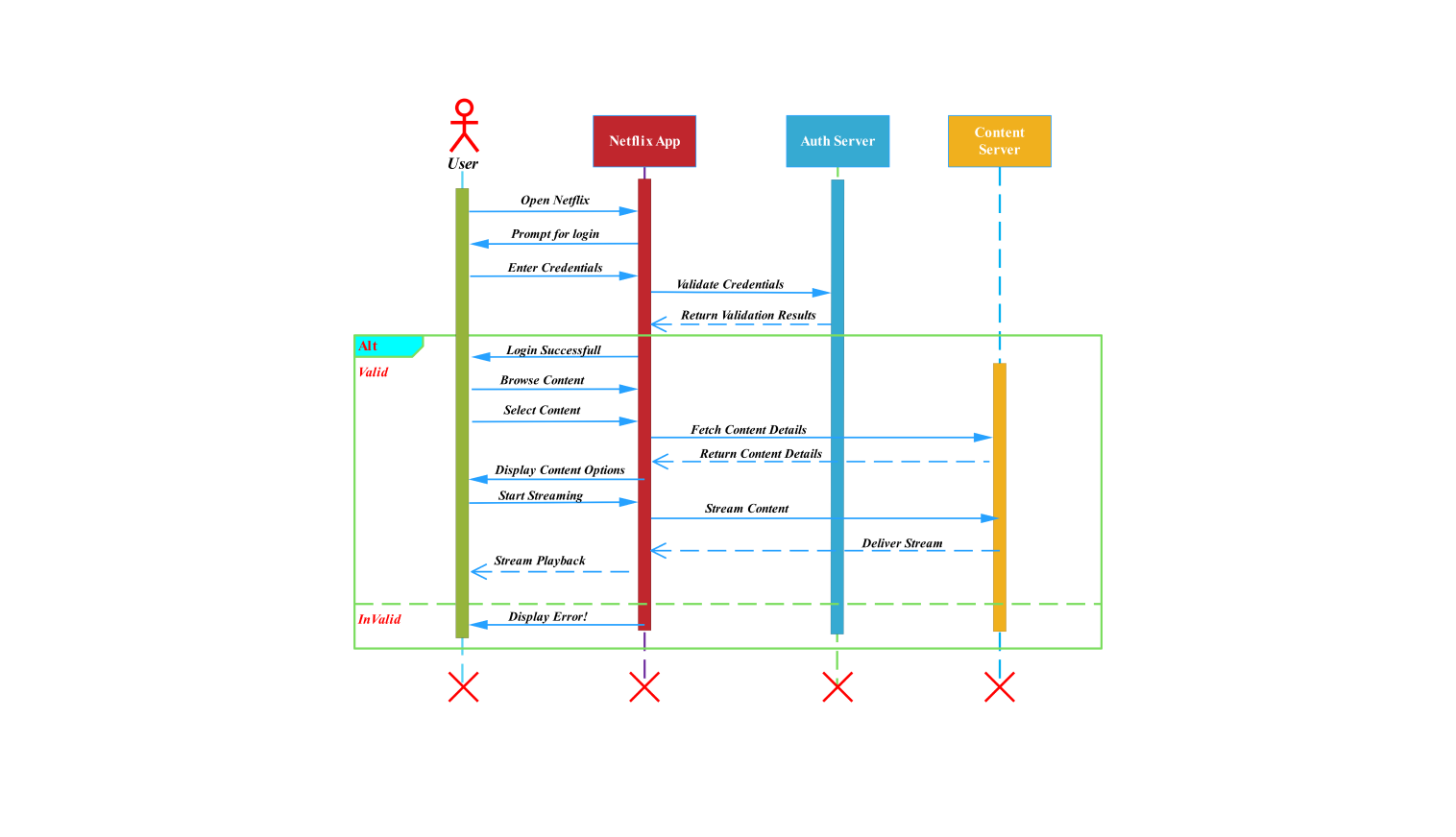
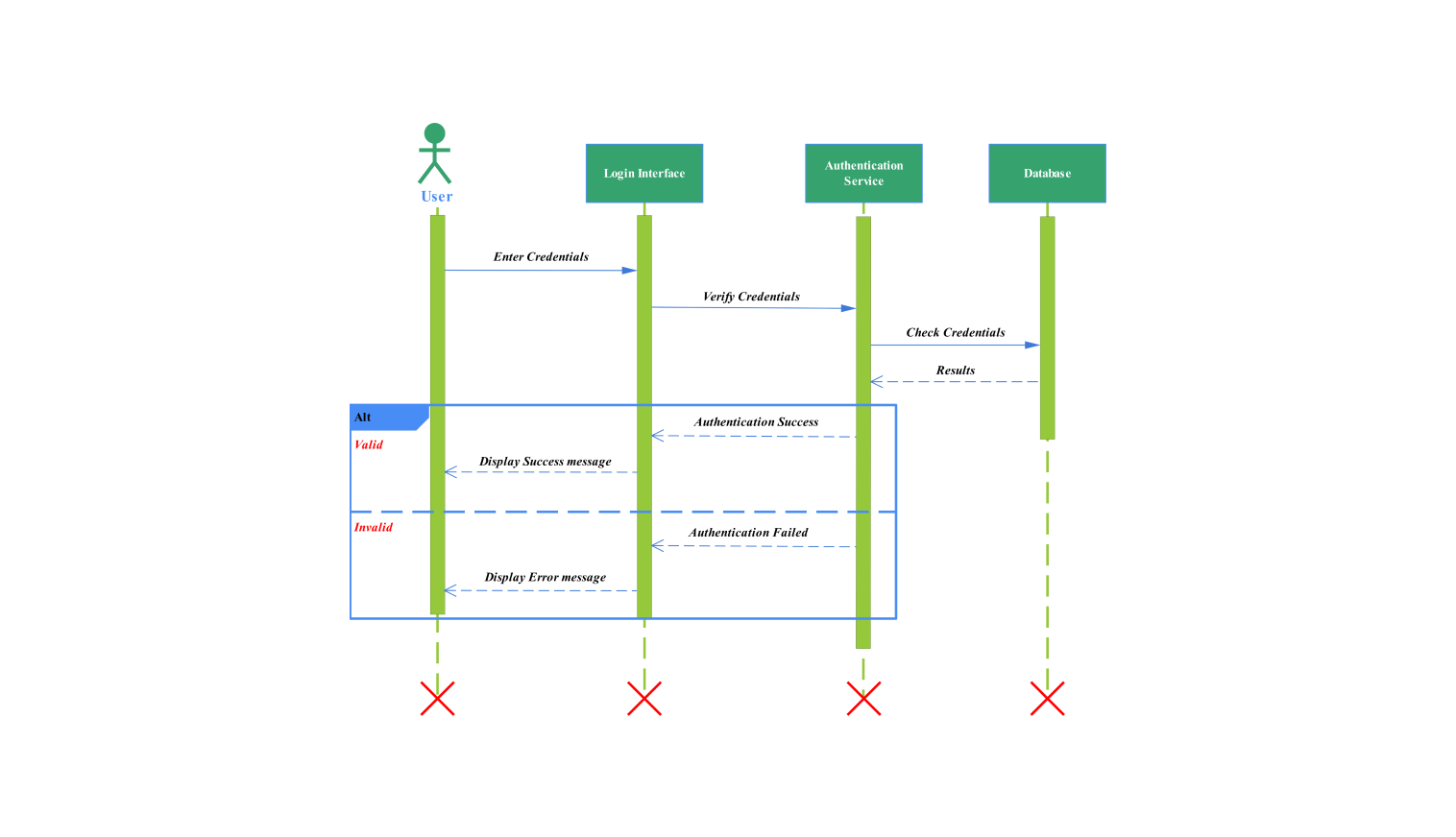
The following diagram shows a user's login authentication. It involves the login agent and the SCA (security certification authority) agent. They validate access control decisions from ACA policy agents. It specifically provides a visual representation of their interactions to secure and validate the authentication process.
In the diagram, the user first requests an agent to grant an identity or do an identification operation. The login agent prompts the user for credentials. As soon as it gets a hold of the hashed credentials, the login agent sends these to the SCA agent.
The SCA agent takes care of certification for the user through verification of credentials. The SCA agent and the ACA policy agent work together to initiate a certification request. The ACA policy agent must look up the user's role.
This step is important for authorizing what the user can and cannot do. The SCA agent receives this request and responds with a list of the user's roles. This will be important in certification, as we will see.
When the SCA agent gets a user role list, it runs a check. It tests for a mismatch between an authenticated user's credentials and their roles and permissions. This step of the sequence diagram is important. It makes sure that only authenticated and authorized users can proceed with the login request.
This diagram now proceeds with two scenarios based on the certification check results. If user credentials and roles are successfully proved, authentication will proceed to the login agent as a success.
After a successful authentication from the identity service, the login agent sends an acknowledgment to that effect back to the user, and access is now granted.
If the authentication fails a message from the SCA agent to the login agent is sent as the certification check is an invalid one (due to incorrect credentials or roles). The login agent then tells the user that authentication has failed and stops access to additional activity.
Interaction-based login processes offer a solid flow. They verify credentials, request info needed for the user's role, and make certification decisions. The diagram adds conditional flows for valid and invalid certification paths.
It ends by granting or denying access. This approach ensures secure user authentication. It checks both roles and credentials against the security layer.
Related templates
Get started with EdrawMax today
Create 210 types of diagrams online for free.
Draw a diagram free Draw a diagram free Draw a diagram free Draw a diagram free Draw a diagram free