Every decision you make carries risk, budget shifts, supplier delays, and tech glitches. A risk register helps you stay one step ahead by clearly mapping these threats. It's a decision-making process integrated within modern project management tools.
Teams that follow this habit handle shifts more easily, face fewer surprises, and move faster. In 2025, the difference between strong and weak projects will be how well they track and share risks.
In this guide, I’ll explain the basics of a risk register and how to make a risk register using EdrawMax in simple steps.
In this article
What is a Risk Register?
A risk register (usually a table or spreadsheet) is a living list of uncertainties that could affect your project, good or bad. Within project management software, it serves as a central view where teams can identify, assess, assign, and track risks over time.
Core Components of a Risk Register
A solid risk register isn’t complete without a few key details. Here’s what you should include:
- Risk ID: A simple tag or number for each risk to help your team refer to it easily in meetings or reports.
- Risk Description: Spell out exactly what could go wrong. Skip vague phrases. Specific risks are easier to manage.
- Risk Category: Sort each risk by type, technical, financial, operational, or external. It helps you spot patterns faster.
- Probability: How likely is it to happen? Use a simple scale like Low, Medium, or High (or numbers 1–5 if your tool allows).
- Impact: What happens if it does occur? Consider the potential effects on your schedule, cost, quality, or reputation.
- Risk Score: Multiply Probability × Impact to see which risks need your attention first.
- Risk Owner: Assign someone responsible for tracking and resolving the issue. Accountability is everything.
- Mitigation Strategy: Note down the steps to reduce the likelihood or mitigate the impact if it occurs.
- Status: Monitor the status of each risk, tracking whether it is open, in progress, under control, or closed.
Why a Risk Register is Your Most Powerful Tool
Proactive Beats Reactive
Without a risk register, most teams spend their days putting out fires. A server crashes, and you panic. A vendor misses a deadline, causing the schedule to collapse.
With a risk register, that chaos turns into control. You spot issues before they escalate into problems. You plan your response when there’s still time to choose.
Everyone Sees the Same Picture
Risks rarely stay in one corner. A delay in development hits marketing. A compliance change touches every department.
When your risk data lives in one place, everyone stays aligned. Stakeholders can instantly view updated scores, owners, and mitigation steps.
Data That Sharpens Every Decision
A solid risk register offers actionable data. You can:
- Rank risks and focus on what matters most
- Spot patterns from past projects
- Allocate time and budget based on real exposure
For cybersecurity teams, this becomes essential. They can map vulnerabilities, assess attack paths, and measure potential impact, all from one place.
Accountability That Actually Works
When nobody owns a risk, it quietly grows until it explodes.
With a risk register, every threat has a name next to it. That person tracks it, updates it, and flags it if things shift.
This clarity builds a culture where people take responsibility instead of hoping someone else will.
How It Drives Real Project Success
Finishing on time, staying on budget, and meeting quality goals, none of that happens by accident.
A risk register helps you control costs, avoid schedule shocks, and maintain standards.
The teams that use it consistently outperform those that don’t. Not because they’re lucky, but because they’re ready.
Types of Risk Registers
Not every team faces the same kind of risk. Here’s a quick way to pick what fits your world.
- Project Risk Register: Ensures a project stays on track, covering time, cost, and scope.
- Program Risk Register: Spots risks shared across multiple projects.
- Portfolio or Enterprise Risk Register: Aligns risks with company-wide strategy.
- IT or Software Risk Register: Logs bugs, tech debt, and vendor dependencies.
- Cybersecurity Risk Register: Guards against data threats and system vulnerabilities.
- Operational Risk Register: Monitors processes, quality, and capacity issues.
- Financial Risk Register: Manages exposure to credit, cash flow, and market swings.
- Health and Safety Risk Register: Protects people by tracking hazards and incidents.
3 Best Templates for Risk Management
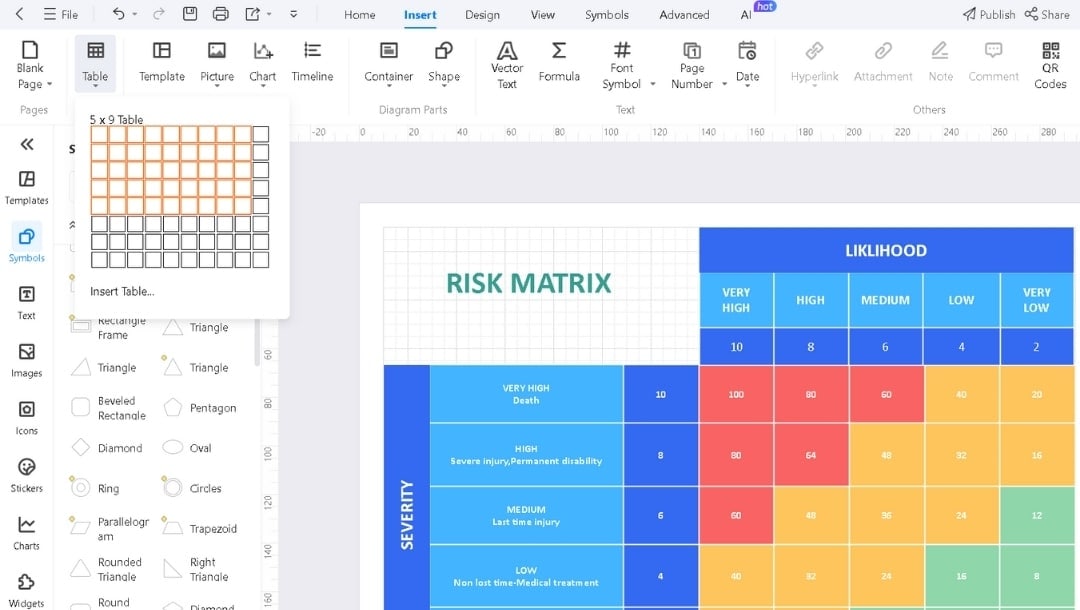
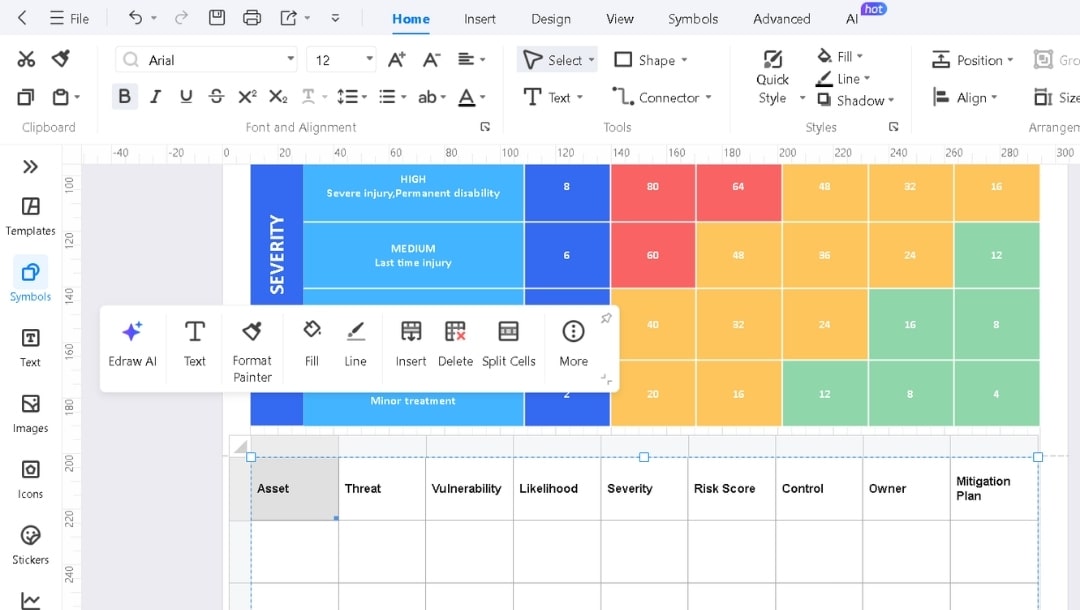
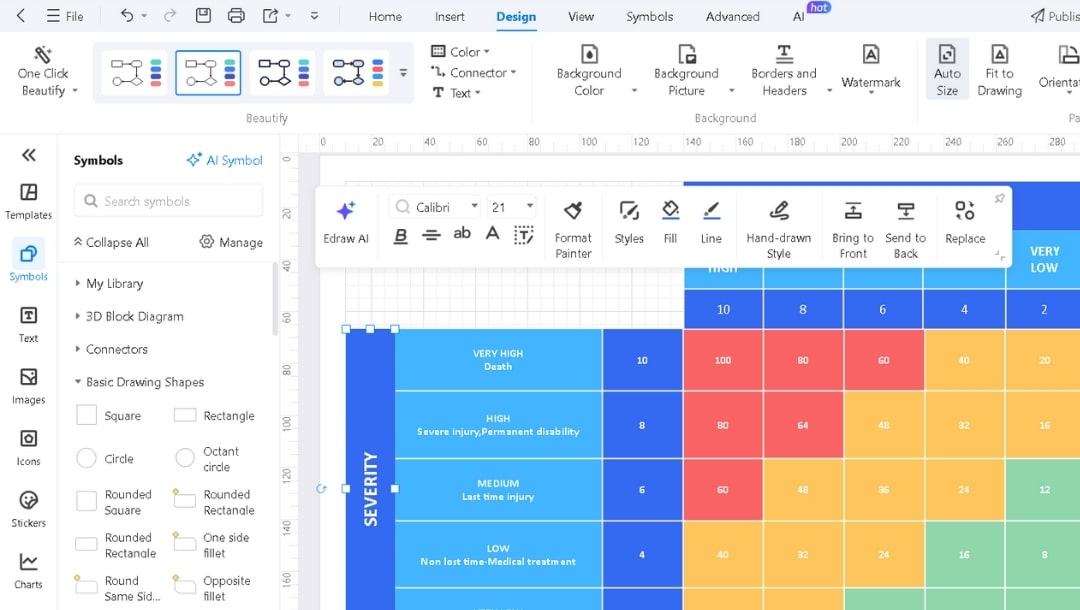
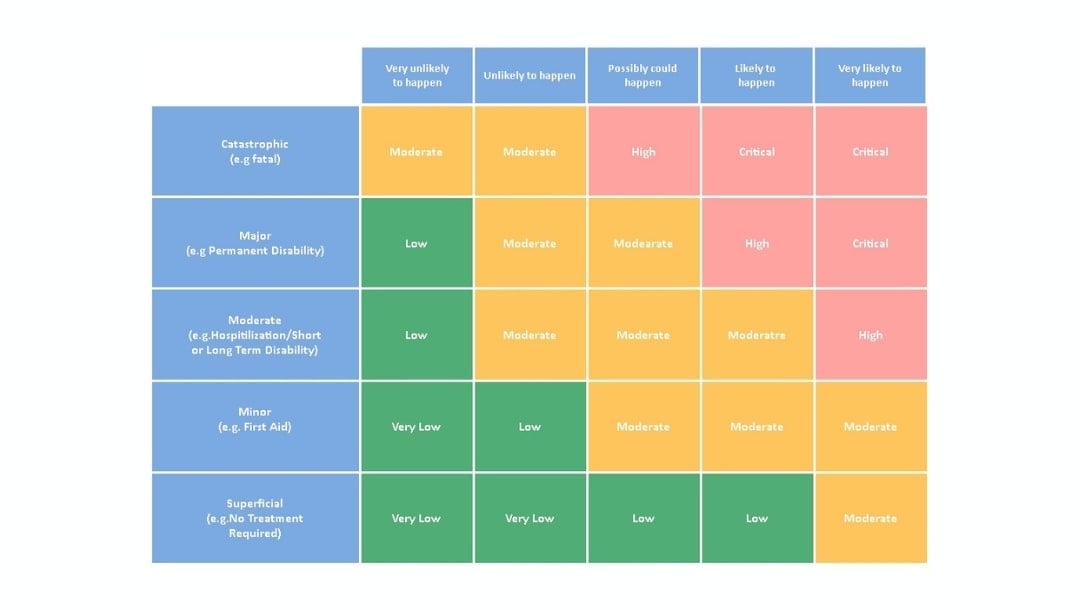
Risk Assessment Matrix
Best for health and safety teams and operational risk managers.
It includes 5×5 grid mapping severity (catastrophic to superficial) against likelihood (very unlikely to very likely), with color-coded risk levels from very low to critical.
Visual priority becomes instant. The color zones show which risks need action now and which can wait. I use this to score every risk before it enters the register.
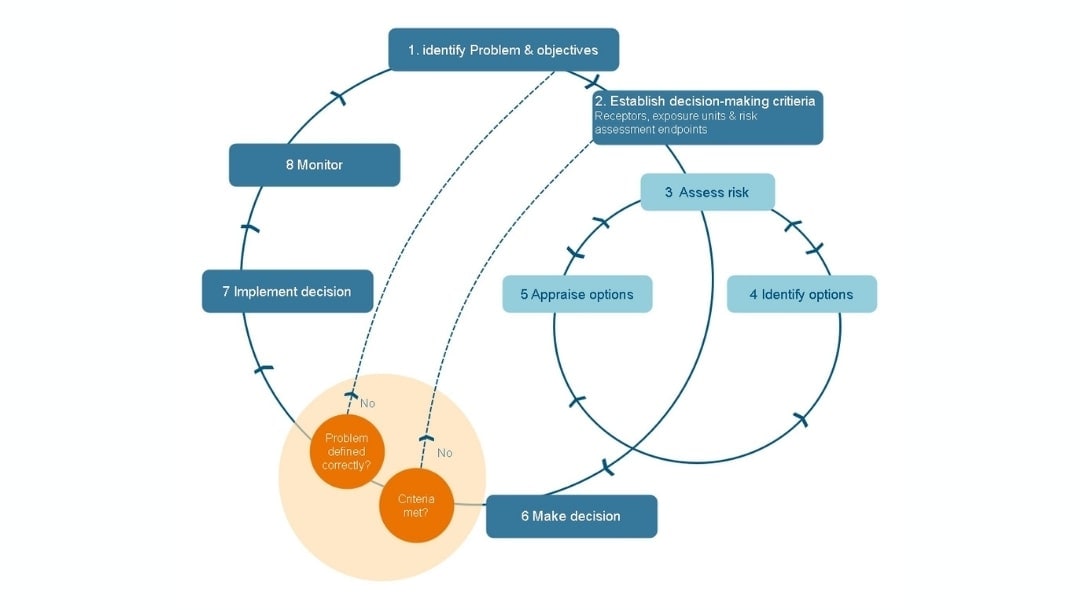
Risk Decision-Making Framework
Best for steering committees and risk governance boards.
It includes an 8-step cycle covering problem identification, criteria setting, risk assessment, option appraisal, decision, implementation, and monitoring with built-in feedback loops.
It turns register data into action. This framework ensures that mitigation plans transition from concept to implementation with clear checkpoints and accountability at each stage.




 below.
below.  below.
below.