Risk assessment is a pivotal process in managing information security risks. ISO 27005 risk management is an international standard that provides guidelines for information security risk assessment and treatment. In this article, we will explore the key aspects of ISO 27005 risk assessment to help organizations implement an effective approach.
In this article
Part 1: What is ISO 27005?

ISO 27005 is a standard published by the International Organization for Standardization (ISO) that offers guidance on information security risk management. Formally named “Information technology — Security techniques — Information security risk management”, this standard outlines the process of risk assessment, risk treatment, risk acceptance, risk communication, and risk monitoring and review.
The current version ISO 27005:2022 focuses on information security risk assessment to complement the broader risk management principles covered in ISO 27001. It provides a structured methodology to assess, treat, and monitor information security risks following principles like confidentiality, integrity, and availability.
Part 2: Role of ISO 27005 Risk Assessment
The core purpose of ISO 27005 risk assessment is to help organizations identify information security threats and vulnerabilities and determine their potential likelihood and impacts. Key roles include:
- Establishing context: Defines scope, parameters, and criteria for risk assessment based on organizational objectives.
- Risk identification: Recognizes threats, vulnerabilities, and impacts that can negatively affect information security.
- Risk analysis: Estimates the likelihood of specific risks occurring and their potential consequences.
- Risk evaluation: Analyzes and compares identified risks using defined criteria to determine risk treatment priority.
Following ISO 27005 guidelines for risk assessment enables organizations to understand security risks and make informed decisions to treat unacceptable risks.
Part 3: Overview of ISO 27005 2022 Framework
The ISO 27005:2022 framework provides an extensive risk assessment model covering key stages:
- Preliminary activities: Determine scope, resources, and high-level requirements.
- Context establishment: Define external and internal parameters to be considered for risk assessment.
- Asset identification: Identify information assets related to the scope and their characteristics.
- Threat identification: Recognize potential threat sources that can exploit vulnerabilities.
- Vulnerability identification: Detect vulnerabilities within the organization that can be exploited.
- Consequence analysis: Estimate adverse impacts or losses from threats materializing.
- Risk estimation: Determine the estimated likelihood of specific risks and their levels of risk.
- Risk evaluation: Analyze risks against defined criteria to prioritize treatment.
- Risk treatment: Select and implement options for mitigating unacceptable risks.
Part 4: Steps of Implementing ISO 27005 Risk Management
Organizations can follow these key steps to implement ISO 27005 risk management:
Form a risk assessment team with appropriate roles like information security manager, risk manager, system owners, auditors, etc.
- Define the scope and boundaries for the risk assessment exercise.
- Identify critical information assets within the defined scope along with their characteristics.
- Recognize relevant threats, existing vulnerabilities, and resulting impacts.
- Estimate the likelihood of specific risks materializing based on vulnerability and threat levels.
- Evaluate each identified risk using qualitative or quantitative methods as defined by criteria.
- Select appropriate risk treatment options such as mitigation, acceptance, avoidance, etc. for unacceptable risks.
- Document risk assessment report with supporting evidence and obtain approval.
- Implement proposed risk treatments and establish monitoring procedures.
- Review and update risk assessment at planned intervals.
Part 5: Difference Between ISO 27005 2022 and ISO 27005 2008
Some key differences between ISO 27005 2022 and ISO 27005 2008 version are:
- Increased focus on integrating risk management into governance processes.
- More comprehensive guidance on risk assessment methodology.
- Introduction of vulnerability identification stage.
- Mandate to establish and maintain a risk management framework.
- More detailed framework for risk evaluation criteria.
- Greater alignment with ISO 31000 for risk management principles.
Part 6: Creating a Risk Management Diagram Using EdrawMax
Edrawmax is an invaluable tool for creating risk management visualizations due to its powerful diagramming capabilities. With an intuitive drag-and-drop interface and a customizable template library, EdrawMax makes it easy for users to develop detailed risk diagrams that enhance their understanding of risk interdependencies and mitigation plans.
Key features like real-time collaboration, automatic styling, and multi-format export empower users to build reusable risk management diagrams that can be leveraged across the organization. Whether creating a risk matrix, flowchart, or relationship map, EdrawMax provides the most essential diagram types and visuals to establish robust risk frameworks and drive better decision-making.
Here are the steps for creating a risk management diagram using EdrawMax:
Step 1:
Launch the EdrawMax tool on your PC. Select relevant templates like risk matrix, flowchart, or relationship map based on need.
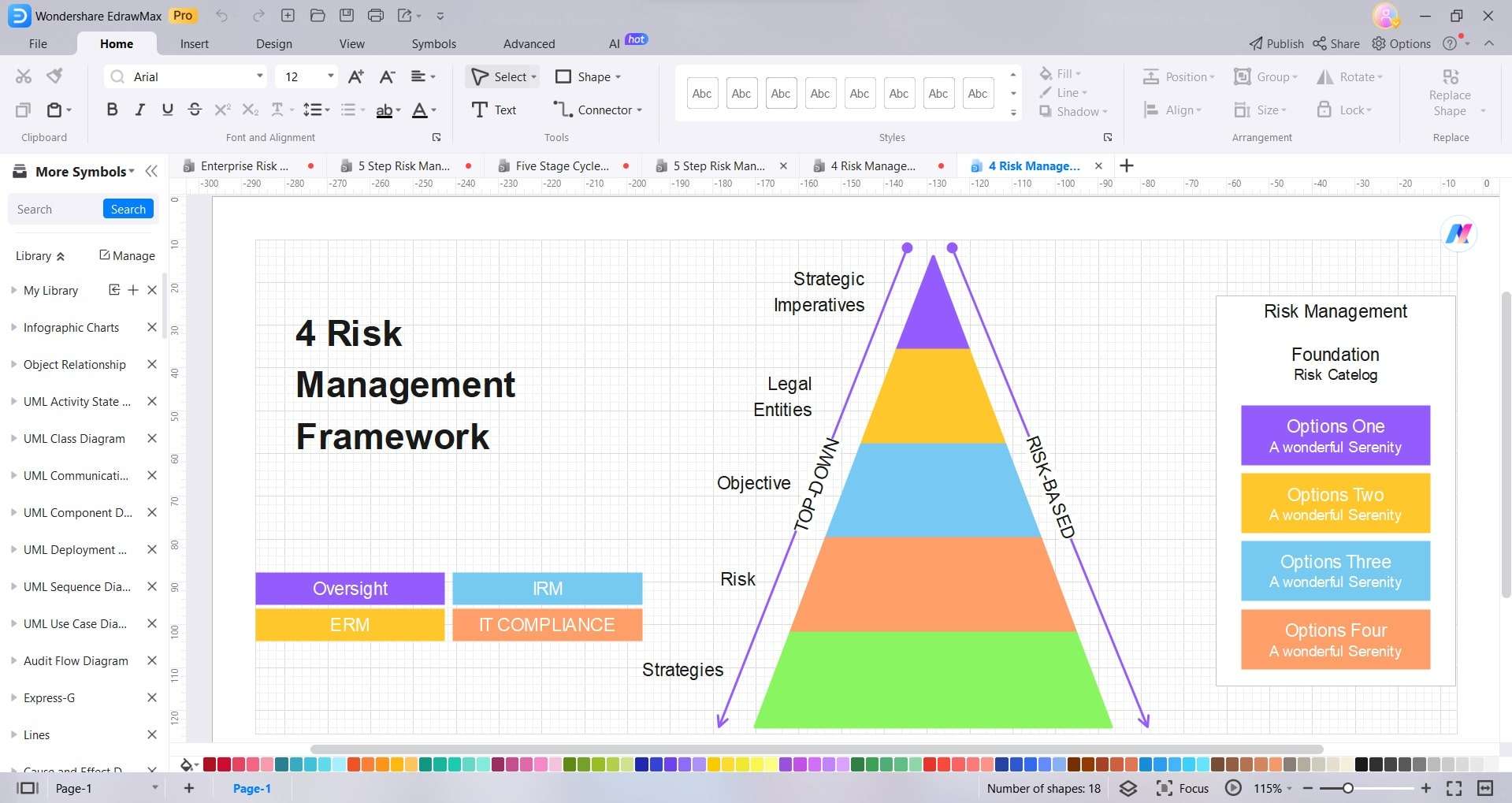
Step 2:
Use drag-and-drop symbols and shapes to represent threats, vulnerabilities, assets, impacts, etc.
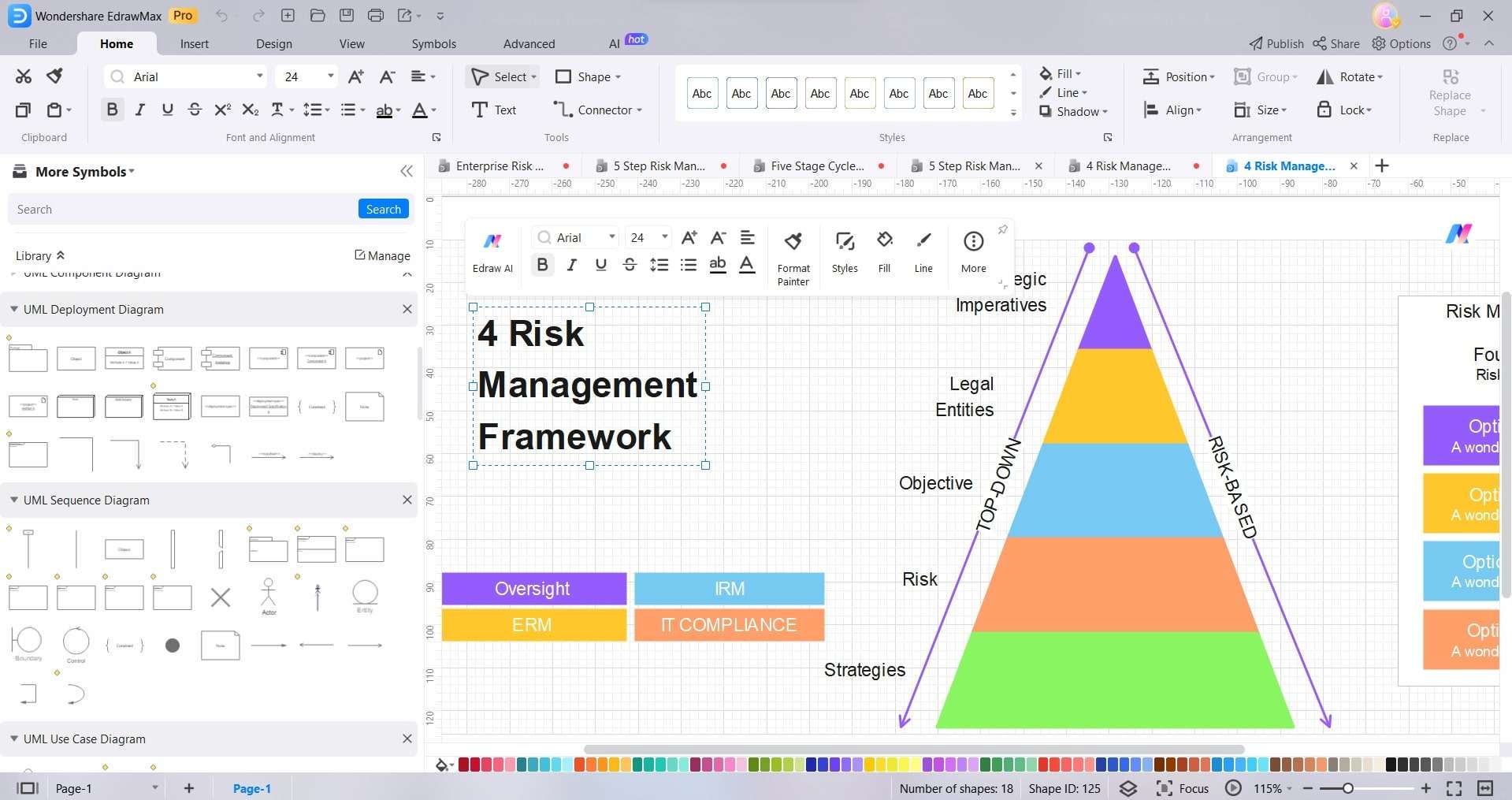
Step 3:
Connect symbols using lines and arrows to depict relationships between elements. Add data and metrics to quantify risk likelihood and impacts.
Step 4:
Customize the diagram with colors, texts, and visuals for clarity.
Step 5:
Share real-time to collaborate with team members. Export diagrams in required format like PDF, PNG, JPEG, etc.
Conclusion
ISO 27005 outlines a comprehensive approach to information security risk assessment, providing the foundation for robust risk management as per ISO 27001. Organizations can follow the guidelines and framework to identify, analyze, and evaluate security risks in alignment with business objectives.
Combined with risk diagrams created in EdrawMax, ISO 27005 enables making data-driven decisions to treat unacceptable risks through a structured methodology. Implementing ISO 27005 risk assessment fosters a proactive culture focused on protecting critical information assets and building enterprise security resilience.