Information Security Risk Management (ISRM) is a comprehensive process that helps organizations identify, assess, and mitigate potential risks to their valuable information assets. ISRM plays a crucial role in safeguarding sensitive data, maintaining business continuity, and ensuring regulatory compliance.
ISRM is a systematic approach to identify, assess, and manage risks to information assets, ensuring their confidentiality, integrity, and availability. It involves evaluating threats, vulnerabilities, and implementing controls to mitigate risks. By adopting IT security risk management practices, organizations can effectively protect themselves from various security breaches, including unauthorized access, and other cyber threats.
In this article
Part 1. How does a Security Risk Assessment work?
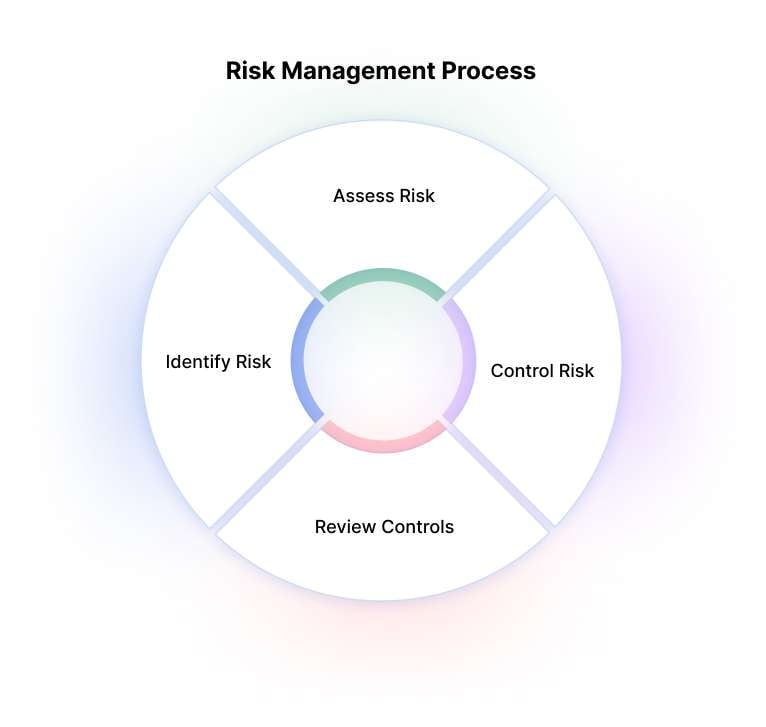
Information Security Risk Management is a necessity for organizations. Information Security Risk Management consists of four key stages.
- Identify Assets: In this stage, organizations identify their critical information assets that require protection.
- Identify Vulnerabilities: Organizations must identify potential weaknesses in their systems, software, networks, or processes that malicious actors could exploit.
- Identify Threats: In this stage, organizations analyze potential threats that could exploit the identified vulnerabilities.
- Identify Controls: Based on the identified assets, vulnerabilities, and threats, organizations determine and implement appropriate controls to mitigate the risks effectively.
A security risk assessment is a fundamental component of ISRM. It enables organizations them to make informed decisions to protect their information assets effectively.
- Scope Definition: Organizations define the boundaries and objectives of the security risk assessment.
- Data Gathering: During this phase, organizations collect relevant information about their information assets, vulnerabilities, threats, existing controls, and historical security incidents.
- Risk Analysis: The collected data is then analyzed to identify the likelihood and potential impacts of different security risks.
- Risk Treatment: Based on the results of the risk analysis, organizations prioritize risks and develop strategies to manage them effectively.
- Monitoring and Review: Once risk treatment strategies are implemented, organizations continuously monitor and review the effectiveness of these measures.
Part 2. What problems do Security Risk Assessment Solve?
Security risk assessments provide several key benefits. They also help in addressing various challenges faced by modern organizations.
- Proactive Risk Management: Regular security risk assessments help identify and mitigate risks before incidents occur, reducing their impact.
- Compliance: Security risk assessments ensure compliance with regulations like GDPR and PCI DSS, avoiding penalties and reputational damage.
- Resource Allocation: Risk assessments prioritize resources effectively by identifying and quantifying risks, allowing efficient allocation of budgets and personnel.
- Stakeholder Confidence: Risk assessments instill confidence in clients, investors, and partners by demonstrating effective risk management, enhancing trust and credibility.
Part 3. Industries Requiring Security Risk Assessments for Compliance
Compliance with regulations is important for industries. Several industries recognize the importance of security risk assessments for compliance purposes.
- Healthcare: Risk assessments ensure compliance, protect patient data, and maintain confidentiality.
- Financial Services: Assessments identify vulnerabilities and ensure security of customer information.
- Government: Assessments identify and mitigate threats to protect national security and citizen data.
- Retail and E-commerce: Assessments secure customer data and protect financial transactions.
To support effective ISRM practices, several cyber security and risk management frameworks have been developed. These frameworks provide organizations with guidelines to manage cyber risks.
- NIST Cybersecurity Framework: Developed by NIST, this framework focuses on five core functions to manage cybersecurity risks.
- ISO/IEC 27001: The standards for setting up an Information Security Management System (ISMS) and safeguarding information assets are laid forth in this international standard.
- COBIT: Developed by ISACA, this framework aligns IT governance with enterprise goals and helps manage information and technology-related risks.
- FAIR: Provides a quantitative approach to measuring and managing information risk, prioritizing security investments based on financial impacts.
5. CIS Controls: A set of prioritized actions to reduce cyber risk, based on industry best practices.
Part 4. Making a security risk management chart with EdrawMax
Wondershare EdrawMax offers a range of templates to help organizations create professional-looking charts quickly and easily. Here are the simple steps to create a security risk management chart using the tool:
Step 1: First, open Wondershare EdrawMax and log in. Enter your login information carefully.
Step 2: You must open a new document after logging in. Just click the "+" symbol next to the "New Document" button, which is located in the interface's upper left corner, to do this.
Step 3: Now, you must select one of the available templates. There are a number of options, each of which offers an appropriate layout and design for your security risk management chart.
Step 4: Once you have selected a template, you will be able to customize the template to meet your specific requirements.
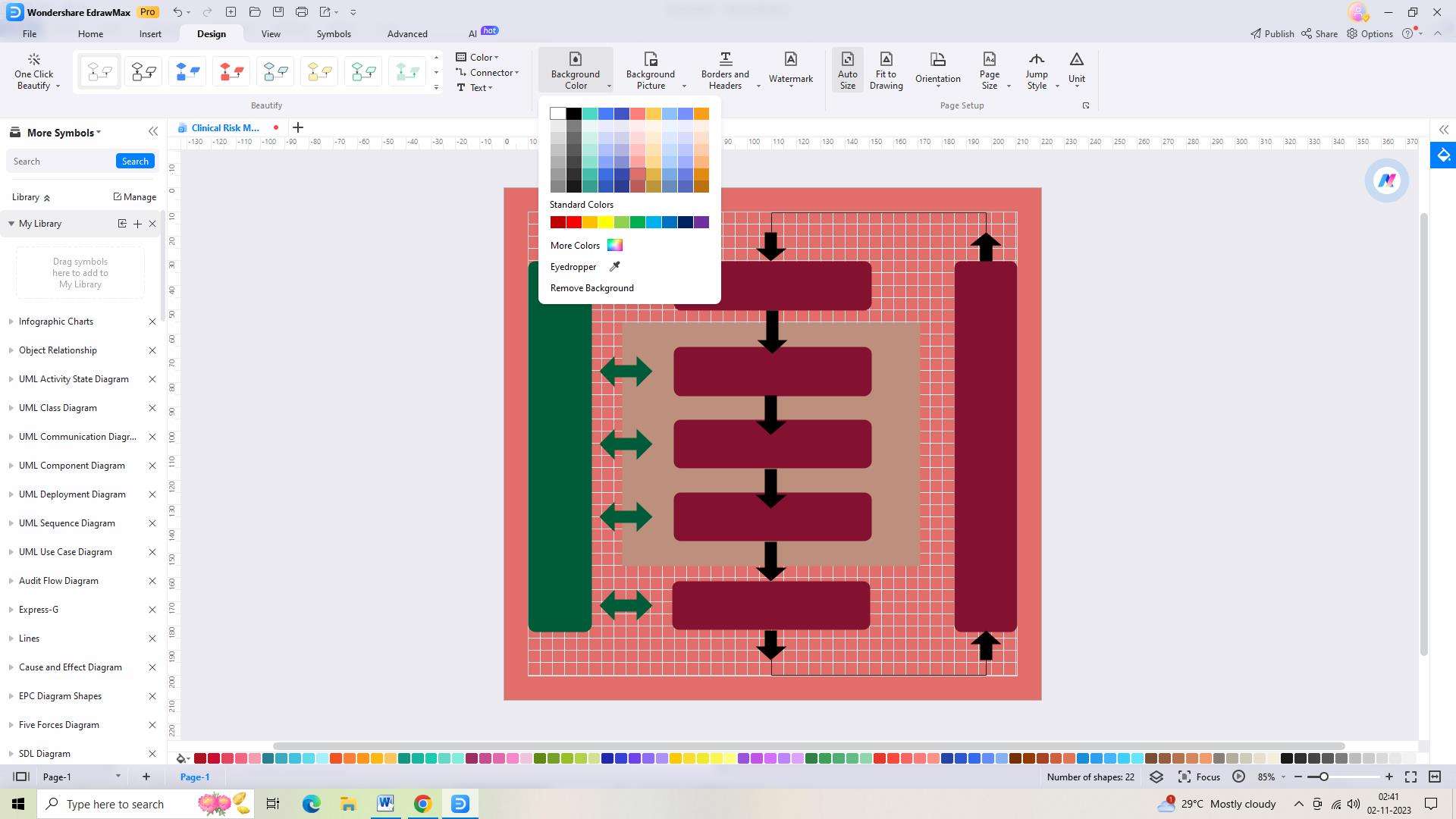
Step 5: The next step is to add any text or labels you wish to include on your chart. To do this, double-click on the text box or label and type in the text you wish to include.
Step 6: Once you are happy with the design of your security risk management chart, you will need to save it. To do this, go to “File,” click on the ‘Save’ button, and select the appropriate format.
Step 7: Next, you will need to export the chart. Go to “File,” click the ‘Export’ button and choose the appropriate format to export your chart in.
Final Thought
Information Security Risk Management is a vital process that enables organizations to protect their valuable information assets and mitigate potential risks. By following the stages of ISRM, organizations can effectively address existing vulnerabilities.