Robust cybersecurity is critical for both government and private sector organizations operating in today's threat landscape. To help organizations manage information security risks, the National Institute of Standards and Technology (NIST) publishes widely adopted standards and guidelines. NIST 800-37 Revision 2 represents a recent update to the seminal Risk Management Framework (RMF) guidance.
This article provides an in-depth look at NIST 800 37 Rev 2, exploring what's changed and best practices for utilizing the new guidance. We'll also highlight how EdrawMax diagramming software can support implementation.
Part 1: What is NIST?
NIST is a non-regulatory federal agency operating under the Department of Commerce. NIST has developed measurement standards and technology programs for over a century that enhance economic security and public safety. In the cybersecurity realm, NIST publishes standards and best practices aimed at both government and industry adoption. These resources are developed through public-private collaboration with leading experts.
Part 2: Overview of NIST 800-37 Rev 2
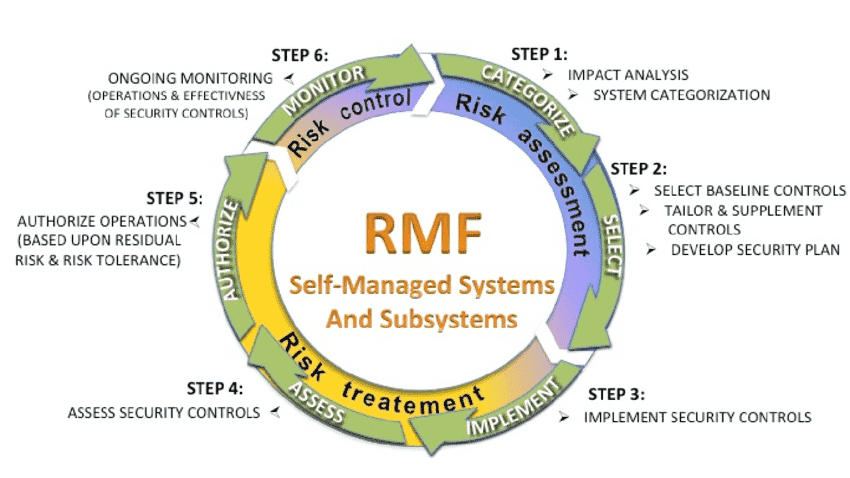
NIST 800-37 Revision 2 represents an update to the popular Risk Management Framework first published in 2010. The 2018 revision aims further to integrate information security into broader organizational risk management activities. It provides guidelines for assessing, selecting, implementing, assessing, authorizing, and monitoring security controls.
While foundational RMF concepts remain unchanged, the update provides clarity and depth to process implementation. The enterprise-level focus aims to facilitate better communication and coordination between senior leaders, risk executives, and system-level personnel.
Part 3: Major Differences Between NIST 800-37 Rev 2 and Rev 1
While Revision 2 retains the same basic 6-step framework, notable enhancements were made throughout:
Step 1: Categorize Systems adds privacy risk assessment guidance
Step 2: Select Controls including impact prioritization for control selection
Step 3: Implement Controls emphasizes the ongoing aspect of implementation
Step 4: Assess Controls introduces methods for dynamic assessment
Step 5: Authorize Systems provides an authorization package checklist
Step 6: Monitor Controls highlights automated and real-time monitoring
Additional key differences include:
- Clearer definitions for key risk management roles
- Alignment with NIST publications including 800-39, 800-160, 800-53 Rev 5
- Added support for privacy controls selection
- Greater detail on control inheritance from common controls
- A new appendix covering supply chain risk management
Taken together, the changes promote enterprise integration, automation, and continuous risk awareness – crucial for modern threat environments.
Part 4: Best Practices for Implementing NIST 800-37 Rev 2
Organizations aiming to maximize their utilization of the updated guidance should consider these best practices:
- Obtain leadership commitment to integrating framework across the enterprise
- Align policy and procedures to RMF roles, responsibilities, and terminology
- Provide adequate training and resources for personnel executing RMF steps
- Inventory systems and components to determine security categories
- Select controls according to a documented, repeatable process
- Utilize automation to streamline assessment, authorization, and monitoring
- Maintain thorough documentation and allow appropriate access
- Normalize assessment processes across system types
- Develop an enterprise-level view of the security posture
- Foster open communication between system owners, operators, and security staff
Organizations that institutionalize these best practices will be well-positioned to maintain a robust security program in the face of evolving threats.
Part 5: Creating a Risk Management Diagram Using EdrawMax
EdrawMax is a visual diagramming platform that can help teams better understand and communicate NIST 800-37 Rev 2 implementation. With EdrawMax, users can select from a library of NIST framework templates to quickly create risk management visualizations.
EdrawMax provides a range of features to create professional NIST framework diagrams efficiently:
- Intuitive drag-and-drop interface.
- Numerous risk management shape libraries.
- Smart drawing aids for alignment and spacing.
- Stylish color themes and custom fonts.
- Ability to export as images, PDFs, or interactive HTML.
With these user-friendly tools, EdrawMax enables both technical and non-technical teams to better grasp complex NIST standards through appealing visual diagrams.
Here are the steps to create a risk management diagram using EdrawMax:
Step 1:
Open EdrawMax and select the "Risk Management" category under diagrams. Browse the templates to find one relevant to your needs, like a NIST 800-37 template.
Step 2:
Customize the template by dragging appropriate shapes from the shape libraries on the left sidebar. Add or remove shapes to match your specific requirements.
Step 3:
Enter text into shapes to label elements or add descriptions. Resize, align and arrange shapes and connectors cleanly on the canvas.
Step 4:
Change shape colors, line styles, and fonts using the formatting panels. Apply custom colors to delineate levels of risk, impacts, etc.
Step 5:
Click "Save As" to store the edited template for future reuse and editing.
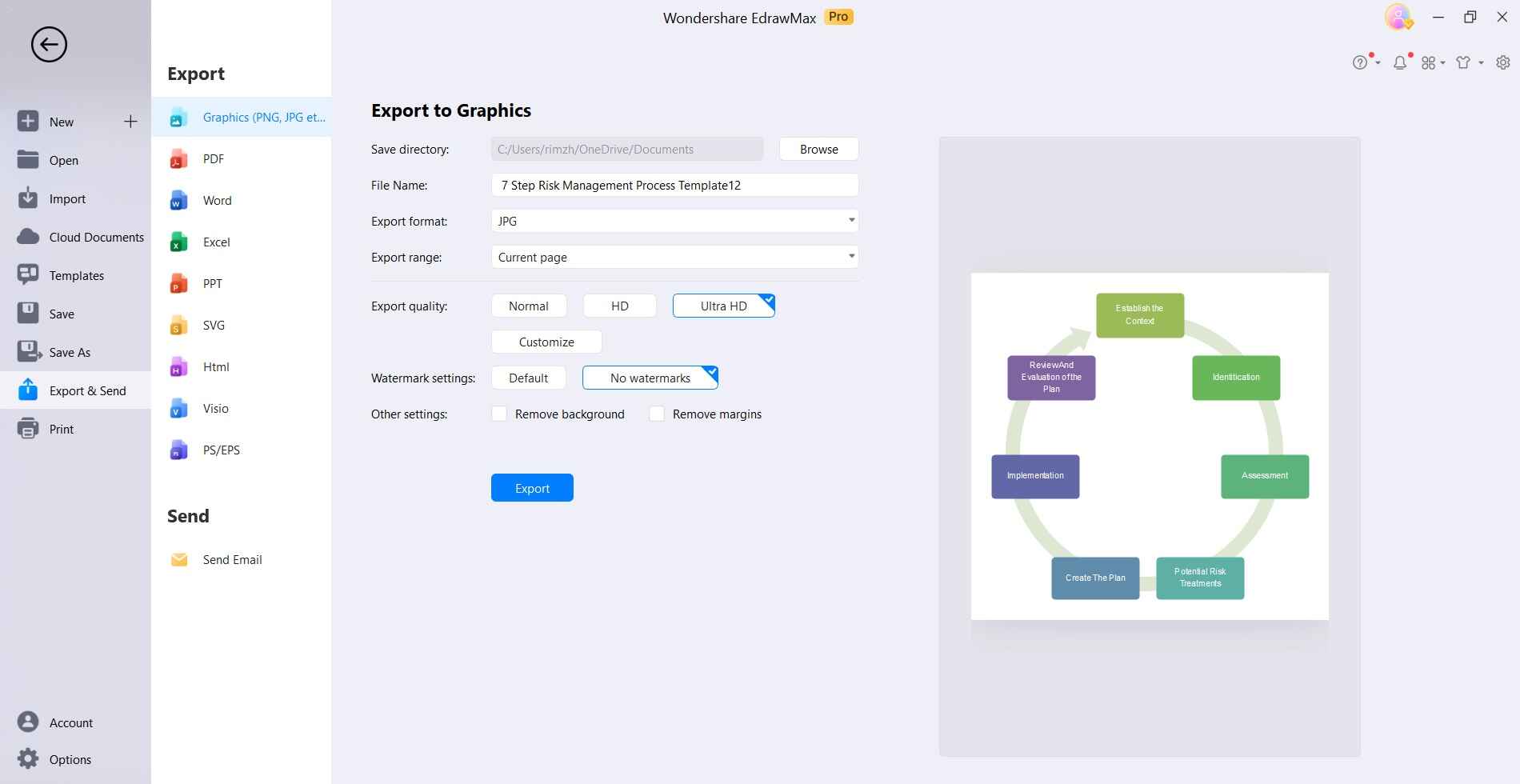
Following these steps allows you to leverage the pre-made templates in EdrawMax to efficiently build custom, publication-ready risk management diagrams that resonate with stakeholders.
Conclusion
NIST 800-37 Revision 2 represents a significant update to the risk management processes supporting cybersecurity. Enhancements in automation, communication, and enterprise view will allow more agile response to emerging threats. Organizations willing to commit resources toward integrated implementation of the guidance can strengthen their security postures considerably.
Finally, diagramming software like EdrawMax fosters an understanding of the framework across a workforce. As risks evolve, both private and public sector teams should tap into the expertise captured in the NIST 800-37 Rev 2 guidelines.