In an era marked by digital interconnectivity, Cyber Risk Management Frameworks have emerged as paramount tools for businesses. These frameworks are designed to systematically identify, assess, and mitigate cyber risks, offering a structured approach to protect sensitive data and operations. This guide delves into the key components and strategies for implementing a robust framework, with a specific focus on addressing third-party cyber risks.
In this article
Part 1. What is a Cyber Risk Management
Cyber risk management is the practice of protecting against online threats. It means looking at how vulnerable your computers and data are to attacks. Then you can take steps to improve security, like installing software to stop viruses or training staff on avoiding hackers. The goal is to stop cyber criminals from stealing information or ruining systems.
With good cyber risk management, companies can avoid many problems from cyber attacks. It helps make sure your business keeps running smoothly even with all the cybersecurity dangers out there today.
Part 2. How a Cyber Risk Management Framework Helps Businesses
Developing robust cyber risk management delivers long-term benefits for businesses by:
- Safeguards Operations: Protects critical data and operations from potential cyber threats.
- Ensures Regulatory Compliance: Helps businesses adhere to data protection laws and industry standards.
- Preserves Reputation: Mitigates the risk of breaches, preserving trust with stakeholders.
- Enhances Third-Party Security: Addresses vulnerabilities associated with external partners or vendors.
- Promotes Proactive Defense: Identifies and mitigates risks before they escalate.
- Safeguards Financial Stability: Reduces the financial impact of cyber incidents, ensuring profitability.
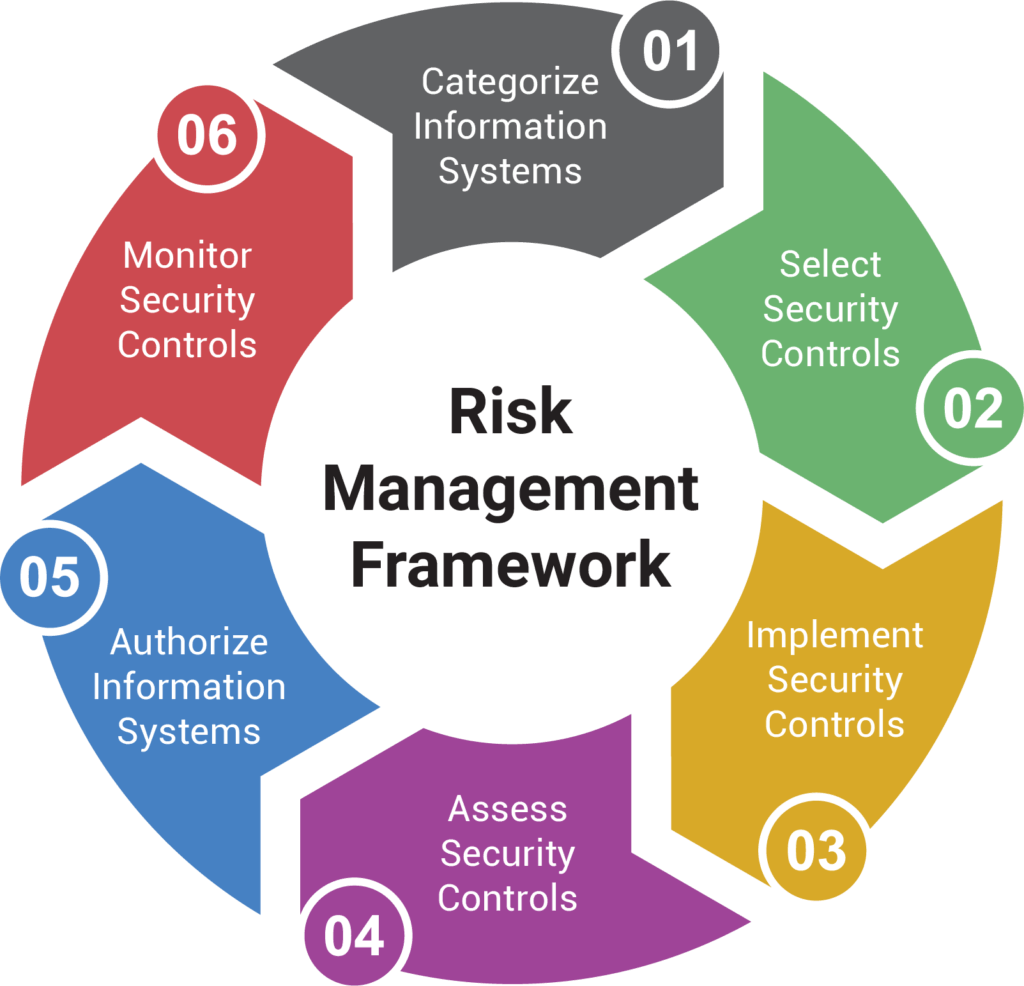
Part 3. Components of Cyber Risk Management Framework
Cyber risk management is crucial in safeguarding organizations from digital threats. A comprehensive framework includes:
- Risk Identification: Identifying potential threats and vulnerabilities.
- Risk Assessment: Evaluating the impact and likelihood of identified risks.
- Risk Mitigation: Implementing measures to reduce risks.
- Incident Response: Establishing protocols for responding to breaches.
- Monitoring and Detection: Employing tools to spot and analyze threats.
- Reporting and Communication: Ensuring transparent communication about risks.
- Compliance and Regulation: Adhering to industry standards and legal requirements.
- Continuous Improvement: Iteratively enhancing the framework based on evolving threats and technologies.
Third-party risk can significantly impact businesses in various ways. Firstly, it exposes organizations to potential data breaches and security lapses, as external partners may have less stringent cybersecurity measures. This can lead to reputational damage, eroding customer trust and loyalty. Financially, it can result in costly legal battles and fines due to non-compliance with data protection regulations.
Moreover, disruptions in the supply chain or service delivery from third-party vendors can lead to operational inefficiencies and revenue loss. As such, thorough due diligence and robust risk management strategies are crucial in mitigating these potential negative impacts.
Part 4. Creating a Risk Management Process Chart Using EdrawMax
Bring your risk management strategy to life with EdrawMax's dynamic process chart creator. Visually mapping out your organization's plan to identify, analyze, and mitigate risks is a game-changer for driving preparedness. With color-coded steps, vivid icons, and clear connectors, you can create an at-a-glance roadmap for navigating threats. See risks collision points come into focus. Watch action plans branch into targeted countermeasures.
Build a risk management chart that doesn't just inform, but energizes your team for readiness. With EdrawMax's real-time collaboration features, update the chart to stay agile as new hazards emerge.
Here are the tips and steps to create a simple risk management process diagram using EdrawMax:
- Define Objectives: Clearly outline the purpose and scope of the risk management process.
- Identify Risks: Thoroughly assess potential threats and vulnerabilities.
- Prioritize Risks: Determine which risks require immediate attention based on impact and likelihood.
- Establish Controls: Implement preventive measures and mitigation strategies.
- Allocate Resources: Ensure sufficient resources are allocated for risk management efforts.
- Monitor and Review: Continuously assess and update the risk management process as needed.
Step 1: Launch the EdrawMax software on your computer. Click on "New" to start working on a blank canvas. Alternatively, switch to the “Template” category from the left menu pane and select a suitable template for the risk management process.
Step 2: Drag and drop the necessary shapes onto the canvas. For a basic risk management process, you'll need shapes for ovals (start/end points), rectangles (process steps), and arrows (flow direction).
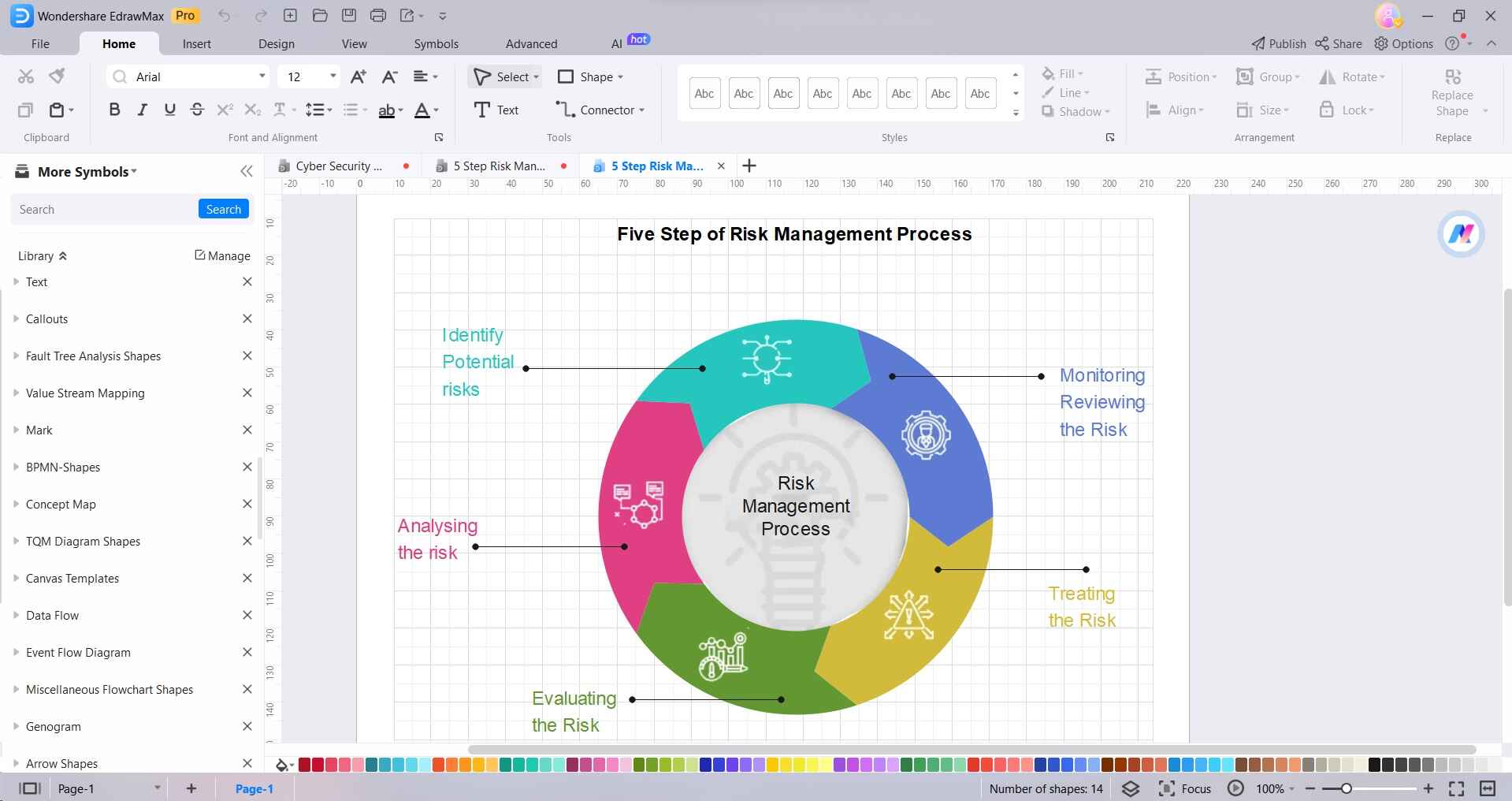
Step 3: Use arrows to connect the shapes in the order they should be followed.
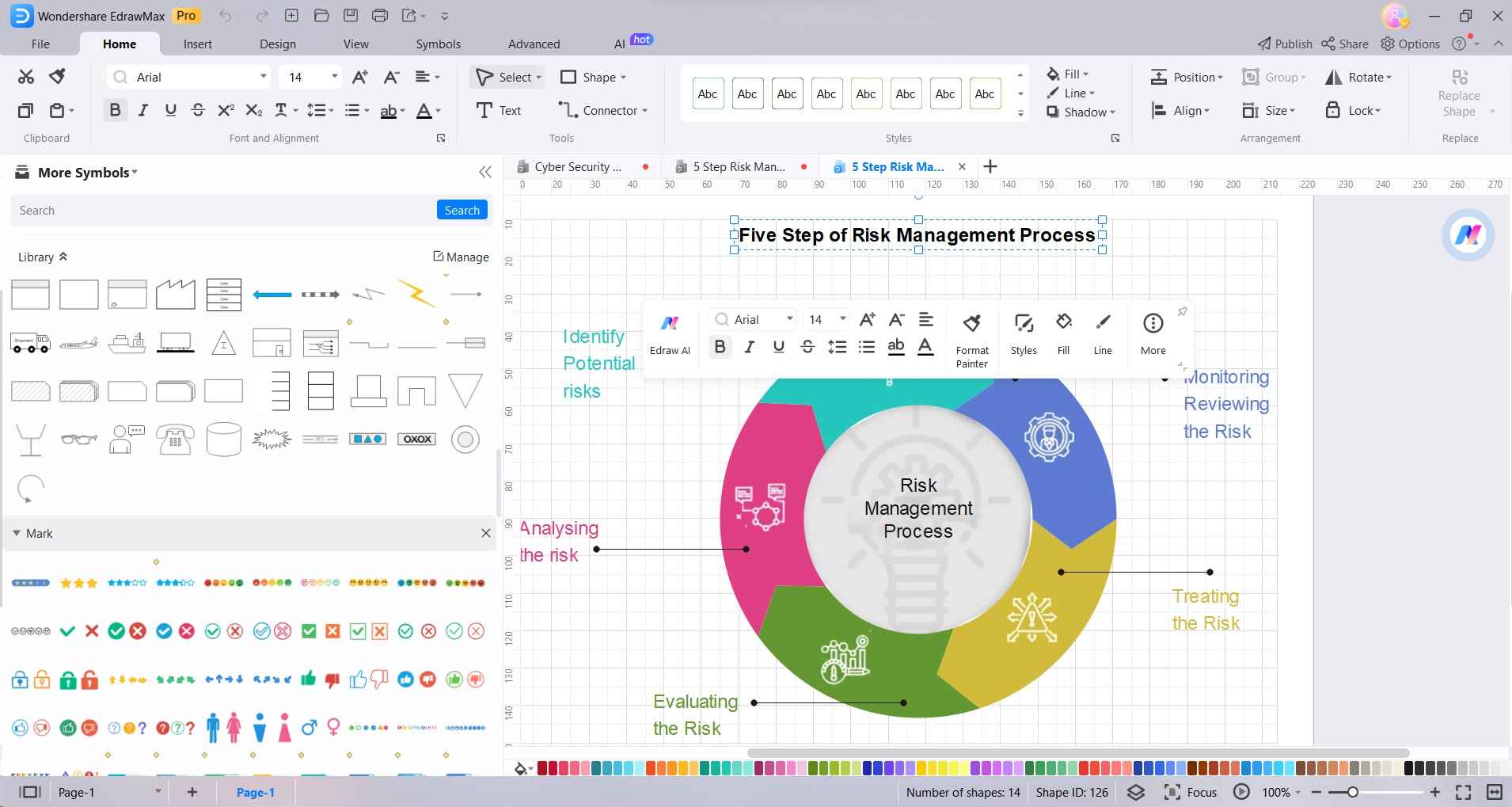
Step 4: Customize the colors, fonts, and styles to make the diagram visually appealing and easy to understand. Double-check the diagram to ensure the flow is accurate and all necessary steps are included. Make revisions if needed.
Step 5: Once you're satisfied with the diagram, save your work in a suitable format. You can export it as an image or PDF for easy sharing.
By following these steps, you'll be able to create a clear and effective risk management process diagram using EdrawMax.
Conclusion
Understanding and implementing a robust Cyber Risk Management Framework is imperative in today's digital landscape. It serves as a strategic blueprint, enabling organizations to proactively identify, assess, and mitigate cyber threats. Utilizing tools like EdrawMax for visual representation enhances the effectiveness of this framework, providing a clear visual guide for stakeholders. By adopting a comprehensive approach to cyber risk management, businesses can safeguard their assets and reputations.