The issue of cybersecurity has gained paramount importance in recent years due to the increasing frequency and complexity of cyber threats. As a result, regulatory bodies such as the U.S. Securities and Exchange Commission (SEC) have provided the SEC cybersecurity proposed rule.
Since releasing its initial guidelines on the subject in 2011, the Securities and Exchange Commission (SEC) has been aggressively combating cybersecurity risks. The significance of cybersecurity risk disclosure for public corporations was emphasized by this recommendation. The SEC underlined again in 2018 how important it is for businesses to promptly disclose significant cyber threats and events.
In this article
Part 1. Evolution of Cyber Risk Management Programs
Over time, companies have recognized the need to develop comprehensive cyber risk management programs to safeguard their critical data and infrastructure. These programs have evolved from mere compliance-focused approaches to more proactive and risk-based strategies.
Today, effective cyber risk management programs incorporate assessments, incident response plans, employee training, and ongoing monitoring of security measures. This evolution reflects the growing understanding of cybersecurity as a dynamic and constantly evolving challenge.

Part 2. How SEC 22e-4 Works
SEC 22e-4, often referred to as the Liquidity Risk Management Program Rule, was introduced to tackle potential liquidity risks faced by mutual funds, exchange-traded funds (ETFs), and other open-end funds.
- Fund Liquidation Determinants: Under SEC Rule 22e 4, fund liquidation determinants play a crucial role in assessing the liquidity of a security. These determinants consider factors such as the time needed to complete a sale, the impact of the sale on the security's market price, and the size of the holding relative to average trading volumes.
- Bloomberg Liquidity Solution: Bloomberg Liquidity Solution is a tool utilized by investment firms to gather data and analyze various liquidity-related aspects of a security. This solution assists fund managers in making informed decisions regarding the liquidity classification of their investments based on factors such as trading volumes, bid-ask spreads, and historical trading patterns.
- Enterprise Delivery: To effectively implement SEC 22e-4, investment companies need to establish an enterprise-wide framework that aligns with the rule's requirements. This entails integrating liquidity risk management into broader risk management processes and ensuring consistent and accurate reporting across the organization.
- Operational Efficiency: Operational efficiency is crucial for successfully complying with SEC 22e-4. It involves streamlining processes related to liquidity risk management, such as data collection, analysis, and reporting. This efficiency allows firms to accurately evaluate the liquidity of their investments and make informed decisions regarding portfolio composition and potential redemptions.
Part 3. Classifying Liquidity in SEC Rule 22e-4
The SEC Rule 22e 4 classifies liquidity into four main categories. These classifications provide investment companies with a standardized framework to assess the liquidity of their holdings and determine whether their risk management procedures adequately account for the potential impact of illiquid investments on fund redemption requests.
- Highly Liquid: Highly liquid refers to securities that can generally be sold or disposed of with minimal impact on their market value within three business days. These securities typically have active trading markets and ample trading volume.
- Moderately Liquid: Moderately liquid securities can typically be sold or disposed of without significantly impacting market value within a week. While they might not have as active a trading market as highly liquid securities, their trading volumes are still substantial.
- Less Liquid: Less liquid securities refer to those that might encounter challenges when attempting to sell or dispose of them without impacting market value within a month. These securities have lower trading volumes or are subject to specific market conditions that limit their liquidity.
- Illiquid: Illiquid securities are typically characterized by a limited trading market or significant restrictions on their sale. These securities, if sold or disposed of, often have a substantial impact on their market value. Illiquid securities are generally harder to value and may take longer to sell.
Part 4. Make a SEC Proposed Cybersecurity Rule Flowchart with Edrawmax
Wondershare EdrawMax provides an intuitive and efficient way to easily create a flowchart as part of the SEC proposed cybersecurity rule, making it quicker and easier to understand and follow. The following are the steps to make such a chart using the tool:
Step 1: You must log in before using a Wondershare EdrawMax template to begin designing the flowchart. Your password and email address should be used to log in.
Step 2: To open a new document after logging in, press the shortcut key "Ctrl+N" or click the plus symbol to the right of the "New" icon.
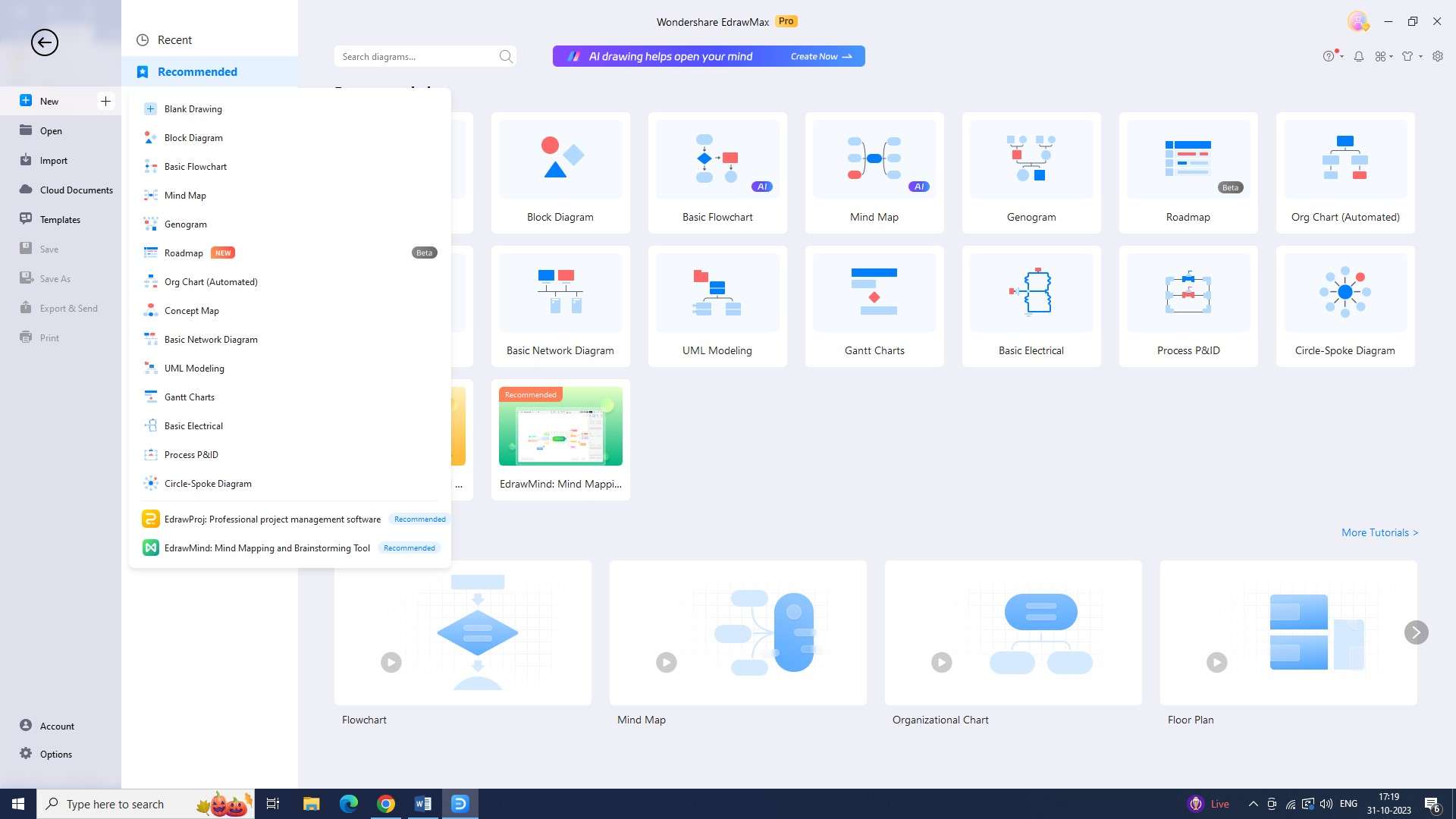
Step 3: Look for an SEC proposed cybersecurity rule flowchart template under the "Templates" section.
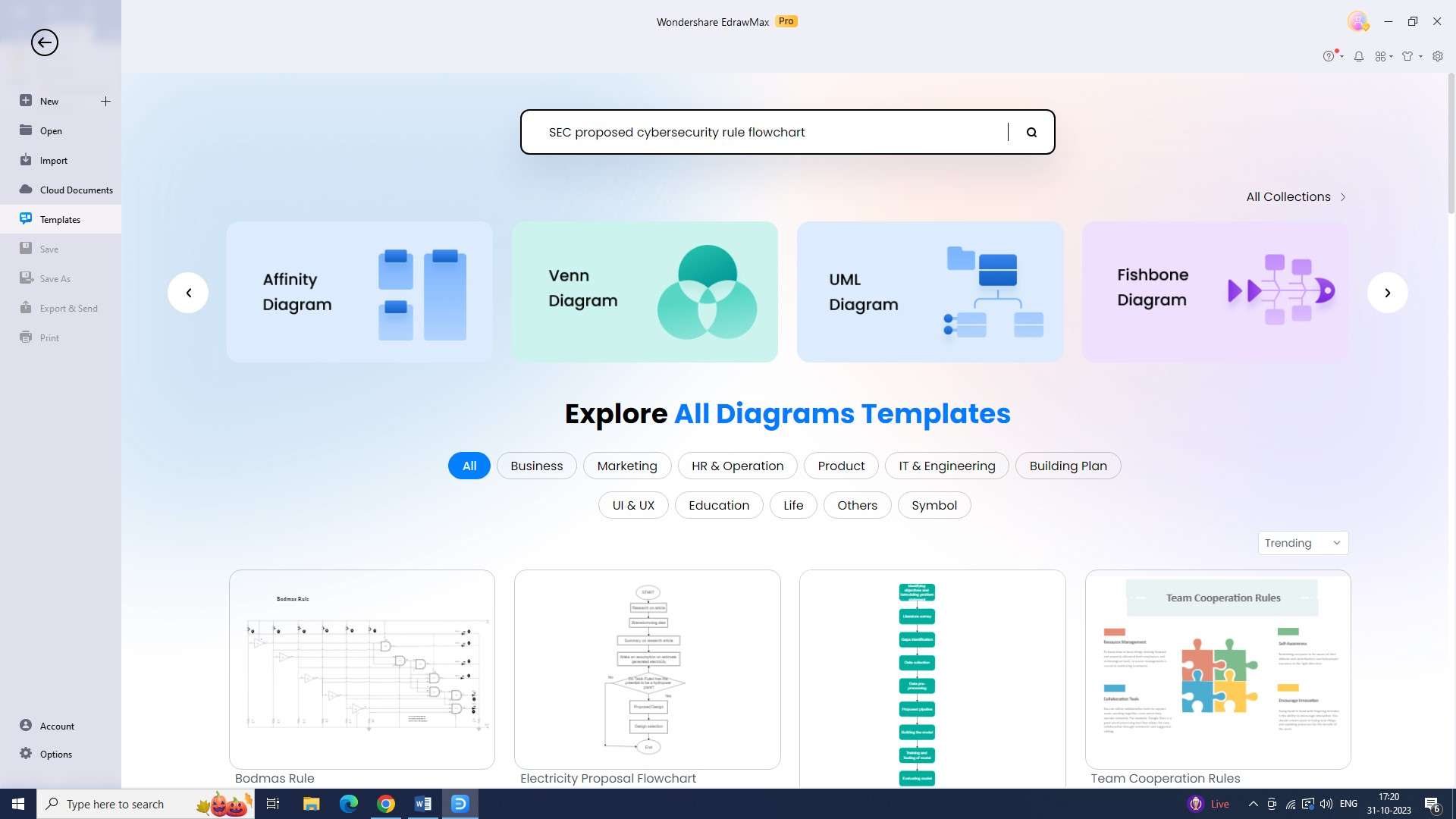
Step 4: Personalize the flowchart to suit your needs. Customization possibilities with EdrawMax are limitless.
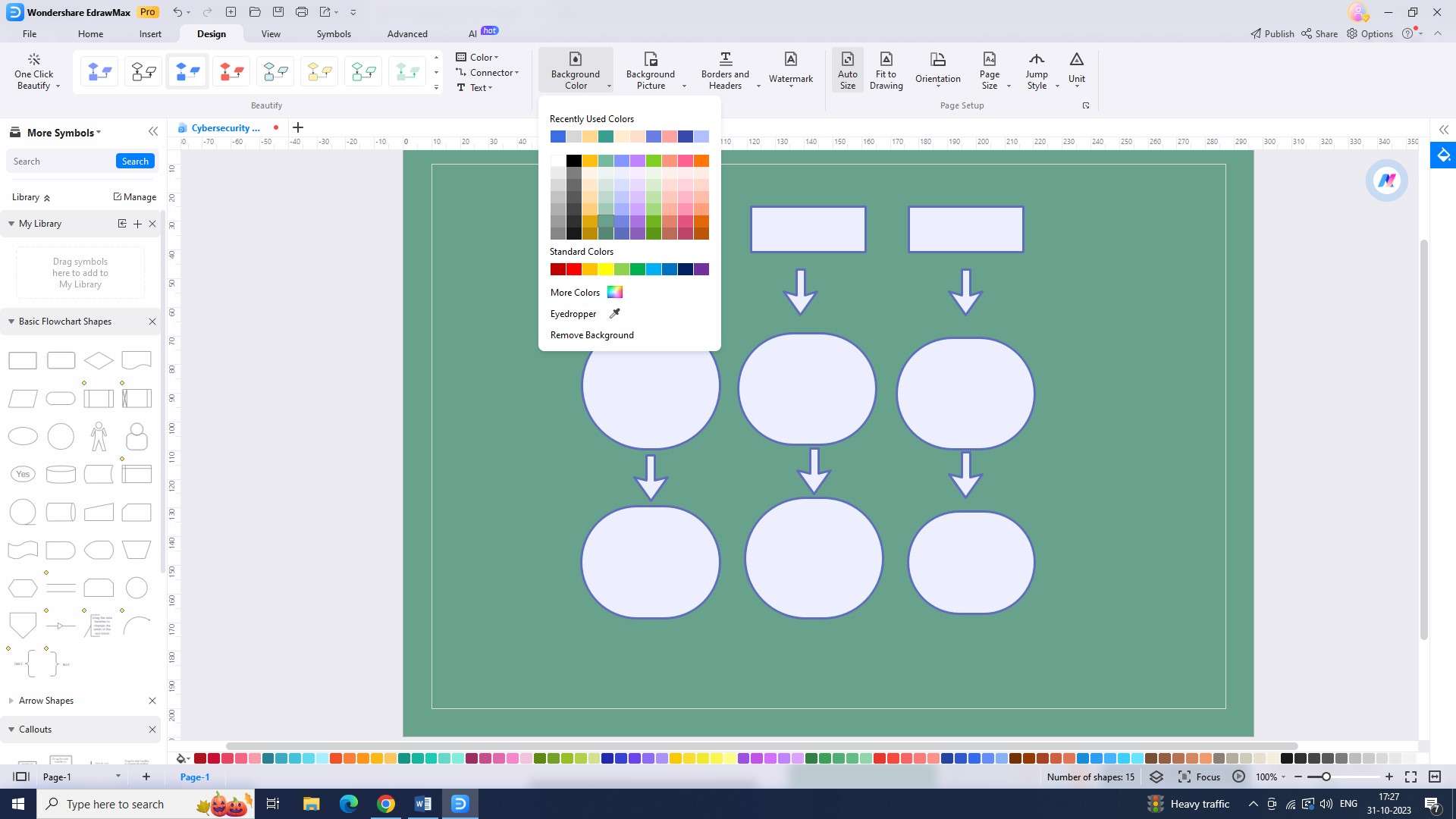
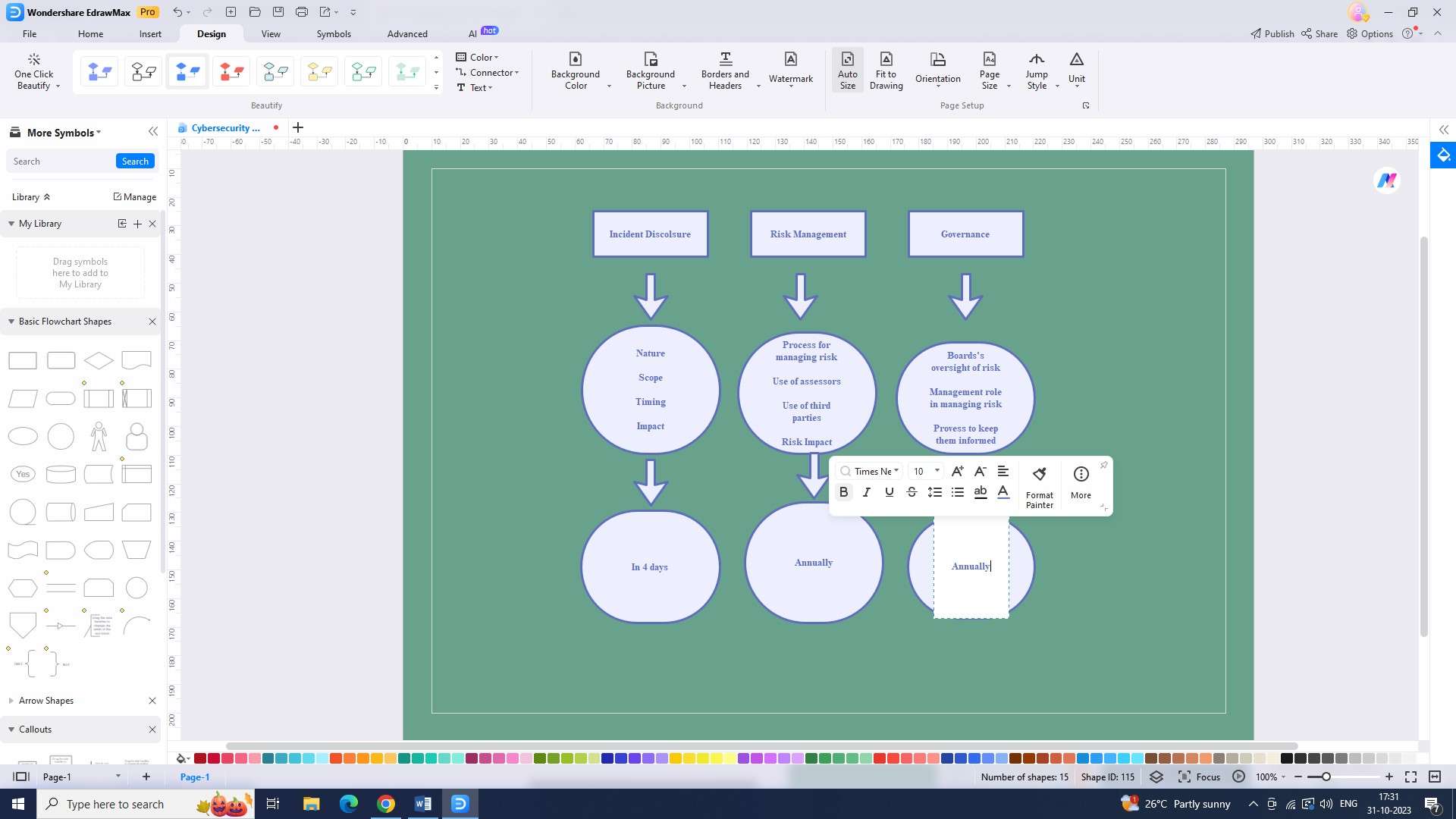
Step 5: Now input the required data into the diagram. Include as much helpful data as possible in your flowchart.
Step 6: The flowchart is now ready to be saved on your computer. Choose the file type you want to save by clicking "Save" under the "File" tab.
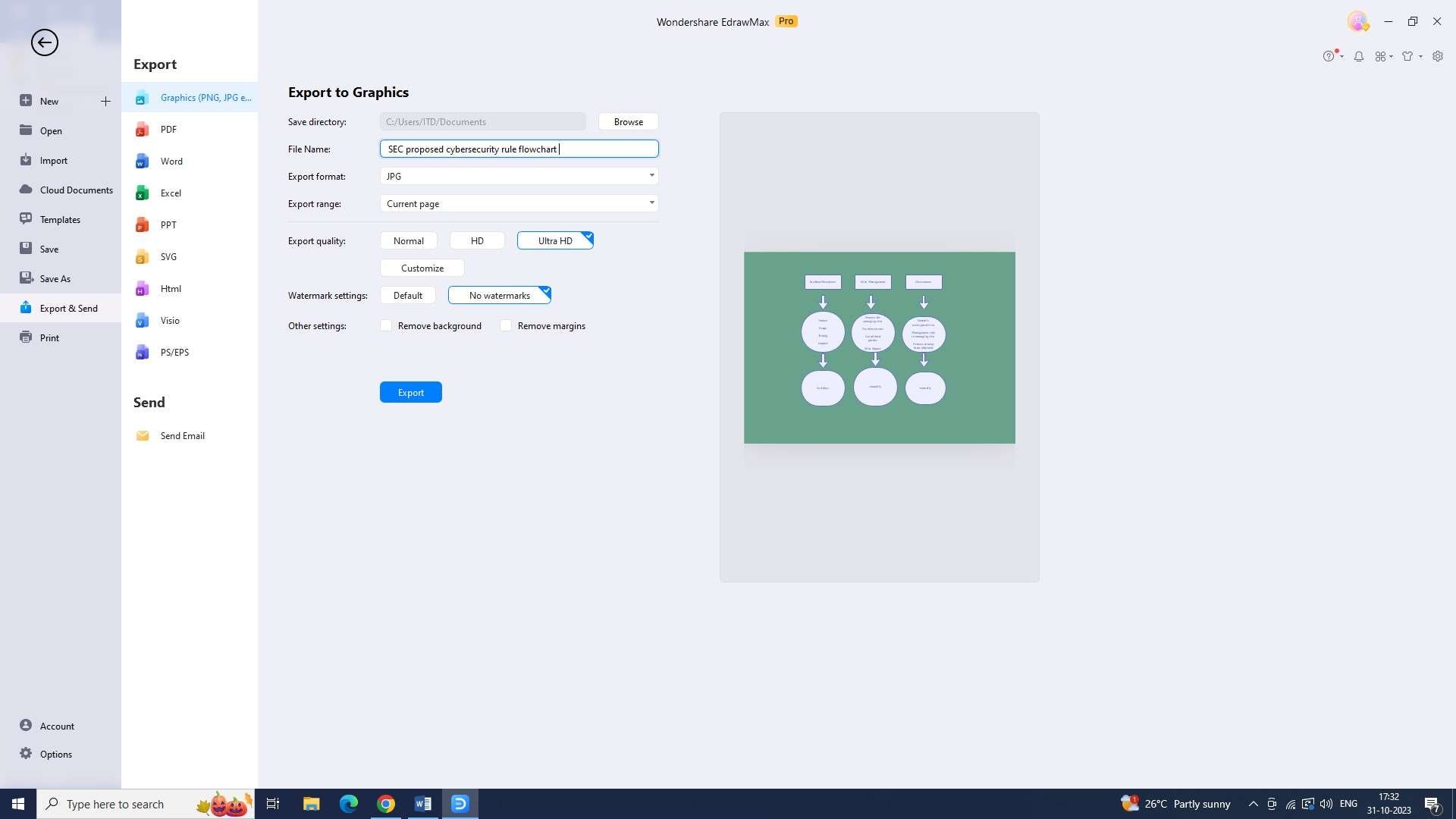
Step 7: You have the option to export your flowchart in a lot of different formats. Click "Export" under the "File" tab and select the appropriate format to export the file.
Conclusion
The SEC's guidance and regulations on cybersecurity have evolved to address the increasing risks faced by investment companies. SEC Rule 22e-4 and its liquidity classification requirements provide investment firms with a comprehensive framework to assess and manage liquidity risk.