- All templates
- Network diagrams
- Network diagram cloud security
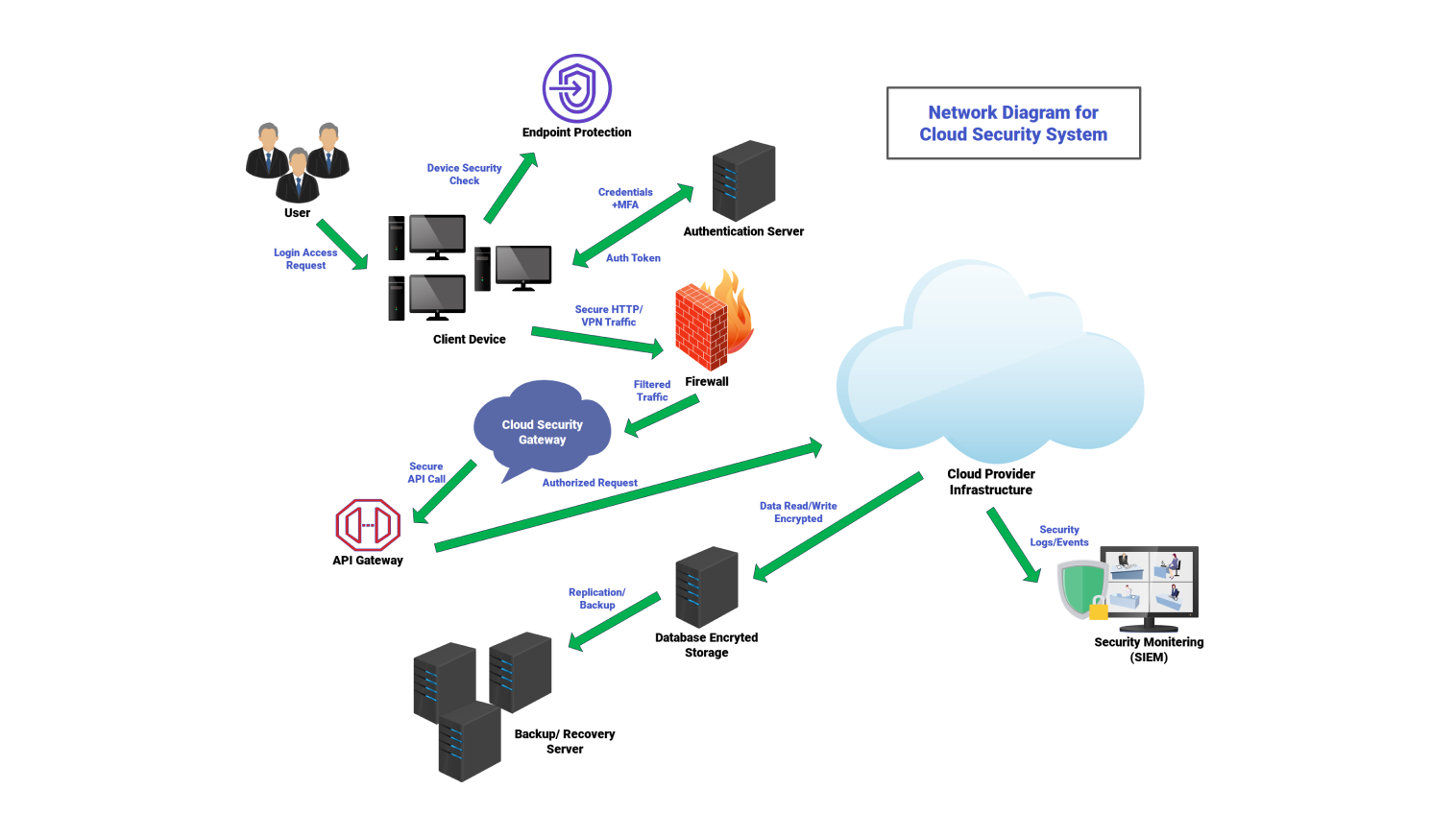
About this network diagram for cloud security
The cloud security system works by handling user access requests. It checks device security and controls how data flows in the protected environment. When a user sends a login access request, the system begins by checking the security status of the device. This means the user must comply with the compliance policies.
Also, it checks if the device environment matches the organization’s security standards. After the device passes these checks, the system processes user credentials. It uses multi-factor authentication. Then, it sends an authentication token back to the device.
The authenticated device sends secure HTTP or VPN traffic to the firewall. All incoming traffic is filtered, inspected, and verified before entering the network. Only approved and cleaned traffic goes to the cloud security gateway. This gateway serves as a central control point for validating authorized requests.
It tracks each session's behavior. It checks that requests meet the rules. It also confirms user access to cloud resources. When an authorized request is accepted, the gateway allows encrypted data to be read and written in the cloud. The cloud stores data and processes user actions. It also keeps all interactions encrypted at all times.
Security logs, events, and monitoring data are gathered. Then, they’re sent to the security operations interface for review. Backend servers receive replicated data or backups to ensure continuity and integrity. This process manages authentication, filters traffic, validates requests, and secures data. It also shows real-time visibility of system operations across all connected parts.
Related templates
Get started with EdrawMax today
Create 210 types of diagrams online for free.
Draw a diagram free Draw a diagram free Draw a diagram free Draw a diagram free Draw a diagram free