- All templates
- Network diagrams
- Network diagram for ddos
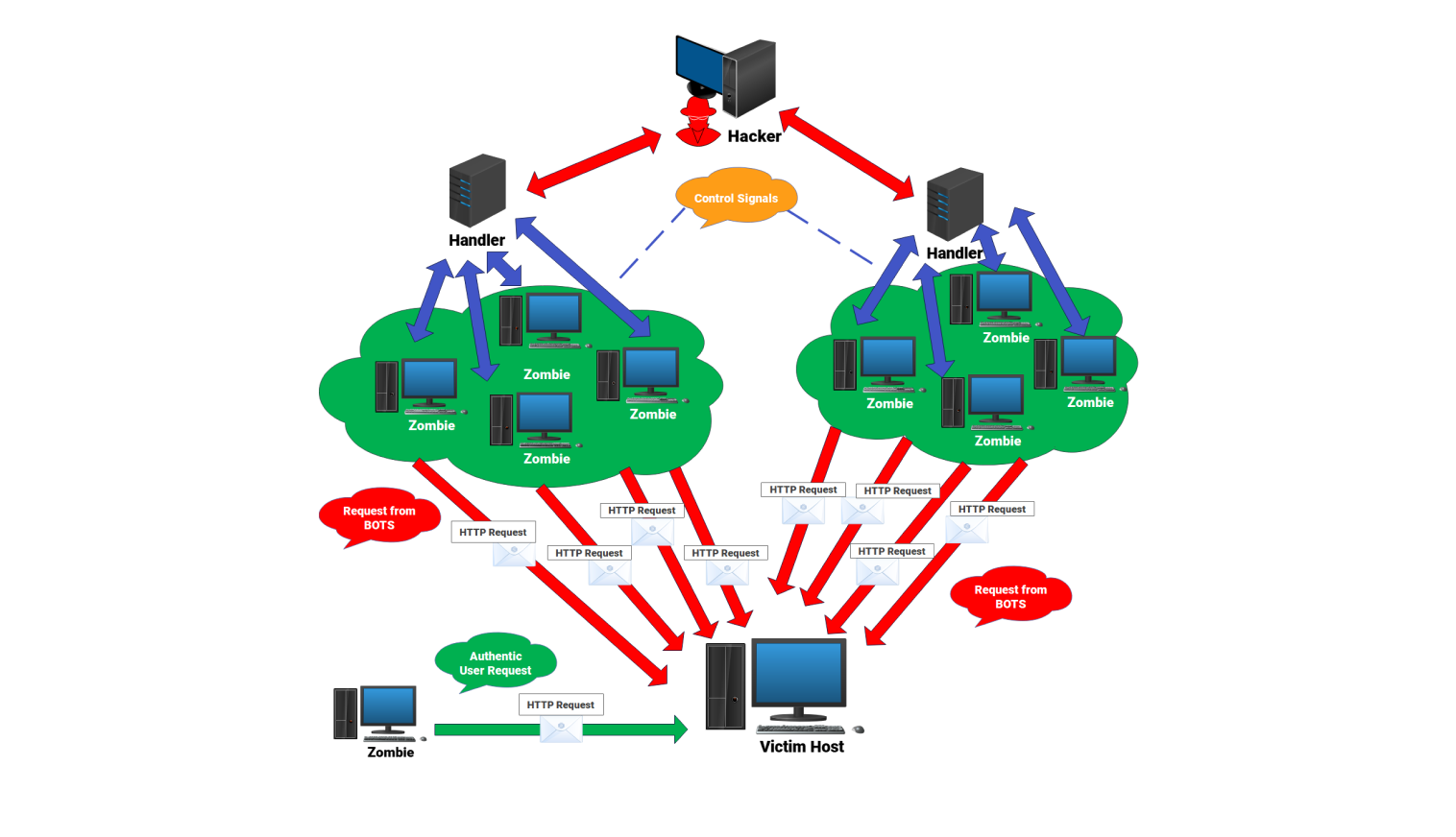
About this network diagram for DDOS
A DDOS attack network uses many hacked devices, known as zombies. These zombies collaborate to overwhelm a target system with excessive requests. The attacker’s control server is located at the center of the network. It sends signals and instructions to intermediary command servers. These command servers send the attacker’s signals to many zombie devices. Each zombie receives commands. These commands tell them when to send requests, how often to communicate, and which target to attack.
When activated, the zombie machines send lots of HTTP requests to the target server. These requests seem like real user traffic, but they come in large volumes. They aim to drain the server's resources. The bots continuously send repeated requests. This builds up traffic along the network path until it gets to the right destination. Authentic user requests try to reach the server too. However, they must compete with the extra load from the bots.
The target server receives requests from multiple directions simultaneously. Its processing capacity starts to fill up when it gets more requests than it can handle. Response times slow down. Legitimate traffic gets delayed or dropped. Eventually, the system becomes unresponsive. During the attack, the zombies keep generating traffic nonstop. They follow the commands from the attacker’s control system.
The whole structure acts like a distributed system. Control signals come from a central point. They spread out to the compromised devices. Then, the devices execute these signals automatically and in sync. This coordination allows the attacker to create a sustained impact on the target. The network focuses on generating, distributing, and saturating requests. This puts constant pressure on the target's resources.
Related templates
Get started with EdrawMax today
Create 210 types of diagrams online for free.
Draw a diagram free Draw a diagram free Draw a diagram free Draw a diagram free Draw a diagram free